Author: Cybernoz
In today’s digital age, having a physical identity is not enough. It is equally important to have a digital identity….
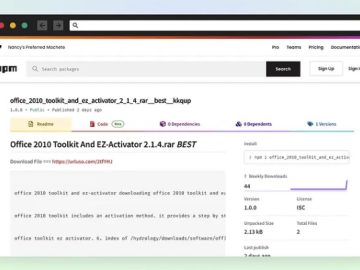
Attackers are exploiting the good reputation and “openness” of the popular public JavaScript software registry NPM to deliver malware and…
Every year hundreds of millions of malware attacks occur worldwide, and every year businesses deal with the impact of viruses,…
Escalating Your Bugs With GDPR Impact Source link
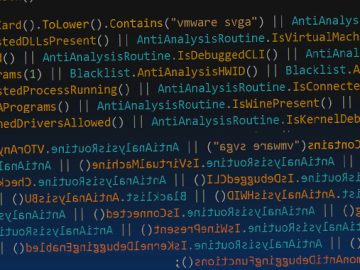
Researchers from Checkpoint found a new and previously unknown ransomware variant dubbed “Rorschach” with highly sophisticated features that target U.S….
How They Got Hacked Episode Fifty Two 52 Source link
Researchers state that Rorschach ransomware has been labelled as the fastest-ever ransomware due to its unparalleled evasion techniques, which have…
Apr 05, 2023Ravie LakshmananCyber Threat / Dark Web The threat actor behind the information-stealing malware known as Typhon Reborn has…
In a major win against cybercrime, the Federal Bureau of Investigation (FBI) seized several domain names tied to Genesis Market,…
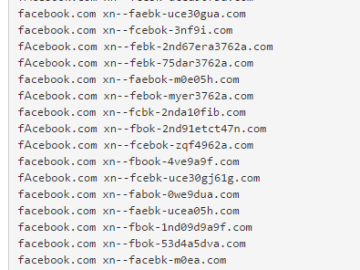
So we’re seeing homograph attacks again. Examples show how ‘apple.com’ and ‘epic.com’ can be mimicked by the use of Internationalized…
The government of Malta has introduced an innovative service to replace human-interfaced customer care with one powered by AI chatbots….
Managing insider risk is becoming increasingly difficult. In fact, insider risk is emerging as one of the most challenging threats…