Amazon Web Services’ Simple Notification Service (AWS SNS) is a versatile cloud-based pub/sub service that facilitates communication between applications and users.
While its scalability and integration capabilities make it a powerful tool for organizations, its misuse by adversaries for malicious purposes such as data exfiltration and phishing has raised significant security concerns.
This article delves into the mechanisms by which AWS SNS can be exploited, explores real-world abuse scenarios, and provides actionable insights into detection and prevention strategies.
By understanding the vulnerabilities inherent in SNS configurations and leveraging robust detection methodologies, organizations can mitigate risks and enhance their cloud security posture.
Understanding AWS SNS: A Double-Edged Sword
AWS Simple Notification Service (SNS) is a cloud-based pub/sub communication service that enables users to send notifications to subscribers via various endpoints such as email, SMS, or mobile push notifications.
It operates on two primary workflows: application-to-person (A2P) and application-to-application (A2A).
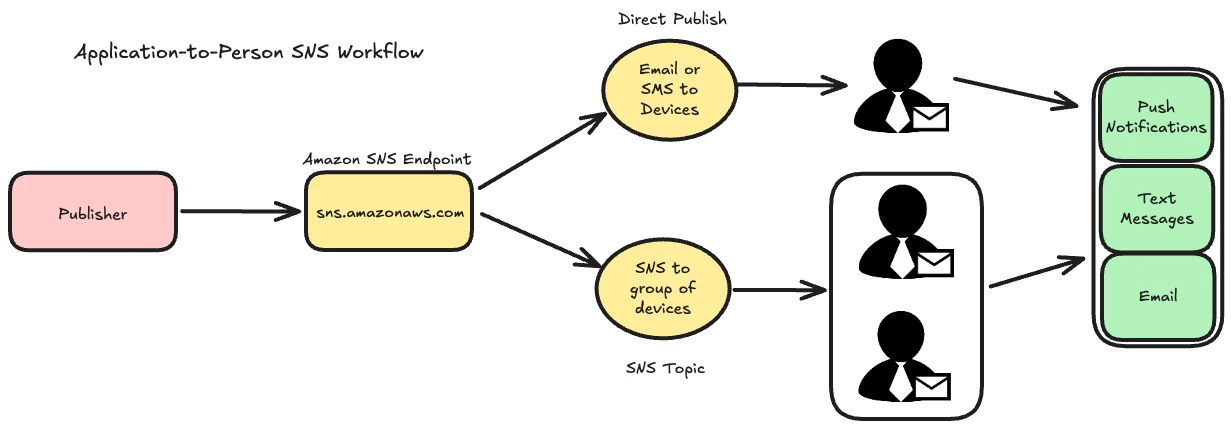
While A2P workflows are designed to integrate seamlessly with AWS services like Lambda and SQS, they also serve as potential vectors for abuse when misconfigured.


Features such as filter policies, server-side encryption (SSE), delivery retries, and dead letter queues (DLQs) enhance the functionality of SNS but can also be exploited by adversaries.
The scalability of SNS allows it to handle massive message volumes without manual intervention, making it cost-effective for organizations.
However, this scalability also means that adversaries can leverage the service for large-scale malicious activities such as phishing campaigns or data exfiltration.
Despite its robust architecture, AWS SNS is susceptible to abuse due to misconfigurations in IAM roles, insufficient monitoring of API actions, and gaps in logging mechanisms.
For instance, adversaries can exploit permissive IAM policies to create topics, subscribe external endpoints, and publish sensitive data without triggering alarms.
The lack of visibility into certain API actions—such as failed Publish requests—further complicates detection efforts.
Encryption mechanisms in SNS focus primarily on securing data at rest using AWS Key Management Service (KMS).
While this ensures the protection of sensitive information such as Personally Identifiable Information (PII), adversaries can bypass these safeguards by exploiting encryption gaps during data transit or leveraging unmonitored endpoints.
Whitebox Testing: Simulating Malicious Behavior
Whitebox testing provides a controlled environment to emulate adversarial behaviors and validate detection capabilities.
Unlike endpoint-based simulations that rely on malware binaries, cloud-focused whitebox testing exploits existing API-driven services through “living-off-the-cloud” techniques.
This approach is particularly effective for analyzing tactics, techniques, and procedures (TTPs) targeting AWS services like SNS.
In a recent whitebox exercise, researchers simulated data exfiltration using SNS by creating a topic that served as a proxy for forwarding stolen credentials to external endpoints.
This method bypassed traditional security mechanisms such as network ACLs and demonstrated the ease with which adversaries could exploit misconfigured infrastructure.
Data Exfiltration Workflow
Adversaries typically follow a systematic workflow to exfiltrate sensitive data via AWS SNS:
- Initial Access: Gaining entry into an EC2 instance through methods like exploiting vulnerable web applications or using stolen credentials.
- Credential Discovery: Identifying sensitive information stored locally in files such as
.envor GitHub credential files. - Topic Creation: Using temporary credentials obtained from IMDSv2 to create an SNS topic.
- Subscription Setup: Registering external email addresses or mobile numbers as subscribers to the topic.
- Data Publishing: Encoding sensitive data in Base64 format and publishing it to the topic for distribution.
This workflow highlights the minimal effort required to stage an attack once initial access is achieved.


By leveraging native AWS services like CLI commands and IAM roles, adversaries can blend their activities into legitimate traffic patterns.
One of the most concerning applications of AWS SNS abuse is its use in smishing (SMS phishing) campaigns.


SentinelOne’s research uncovered instances where adversaries employed Python-based tools like SNS Sender to distribute fraudulent messages at scale using compromised AWS credentials.
These campaigns leveraged authenticated API requests to bypass safeguards and send phishing messages impersonating trusted entities.
The success of such campaigns hinges on the adversary’s ability to establish production-level messaging permissions within AWS End User Messaging services.
This requires regulatory approval for origination identities and carrier pre-approval for high-volume SMS messaging a hurdle that sophisticated attackers can overcome by compromising accounts with pre-existing permissions.
While the abuse of AWS SNS presents significant advantages for adversaries—such as blending into legitimate traffic and bypassing egress monitoring it also poses challenges:
- Initial Access: Exploiting vulnerabilities in EC2 instances or acquiring credentials through social engineering.
- Session Persistence: Maintaining active sessions amidst robust endpoint protections.
- Infrastructure Setup: Configuring IAM roles with permissive policies for SNS actions.
- Sandbox Restrictions: Overcoming limitations imposed by AWS on new accounts restricted to SMS sandbox mode.


These challenges underscore the importance of proactive security measures such as hardening IAM policies and monitoring CloudTrail logs for anomalies.
Detection Strategies and Threat Hunting
CloudTrail audit logs serve as a vital resource for detecting unusual API actions related to SNS abuse.
By focusing on assumed roles attached to EC2 instances, security teams can identify anomalies such as rare topic creation or subscription events.
Detection rules can be crafted using Elastic’s New Terms logic to flag first occurrences of suspicious activities:
- Topic Creation by Rare User: Identifying when an assumed role creates an SNS topic unexpectedly.
- Subscription with External Email: Monitoring subscriptions that specify external endpoints.
- Message Publishing Spikes: Detecting sudden increases in direct-to-phone messaging activity.


These rules enable organizations to pinpoint potential abuse scenarios while minimizing false positives through contextual analysis.
Hunting Queries
Threat hunting queries provide deeper insights into potential compromises by parsing CloudTrail logs for specific attributes such as user-agent strings or request parameters.
For example:
- Rare Topic Creation: Aggregating data based on EC2 instance IDs and regions to identify unusual activity.
- Email Subscriptions: Filtering subscriptions by protocol type to detect unauthorized external endpoints.
- Direct Messaging Spikes: Tracking Publish actions with phone numbers in request parameters to uncover smishing campaigns.


These queries help security teams prioritize investigations based on anomalous signals while refining detection logic over time.


AWS SNS is a powerful communication tool that offers immense utility for organizations but also presents significant risks if left unmonitored or misconfigured.
The research outlined above highlights how adversaries can exploit its features for malicious purposes such as data exfiltration and phishing campaigns.
By understanding these vulnerabilities and implementing robust detection strategies using CloudTrail logs and threat hunting queries, organizations can mitigate risks effectively.
Key recommendations include:
- Hardening IAM policies with principle-of-least-privilege (PoLP).
- Enabling comprehensive logging mechanisms across CloudTrail and CloudWatch.
- Crafting anomaly-based detection rules tailored to organizational contexts.
- Conducting regular whitebox testing exercises to validate security controls.
As cloud environments continue to evolve, staying proactive in monitoring emerging threats will be crucial for maintaining robust security postures against adversarial abuse of services like AWS SNS.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!


