Category: CyberSecurityNews
SolarWinds has released an advisory regarding a security incident involving the Salesloft Drift integration for Salesforce, which led to unauthorized…
The cyberthreat landscape has witnessed the emergence of another sophisticated ransomware operation as GOLD SALEM, a new threat actor group…
The Russian covert influence network CopyCop has significantly expanded its disinformation campaign, establishing over 200 new fictional media websites since…
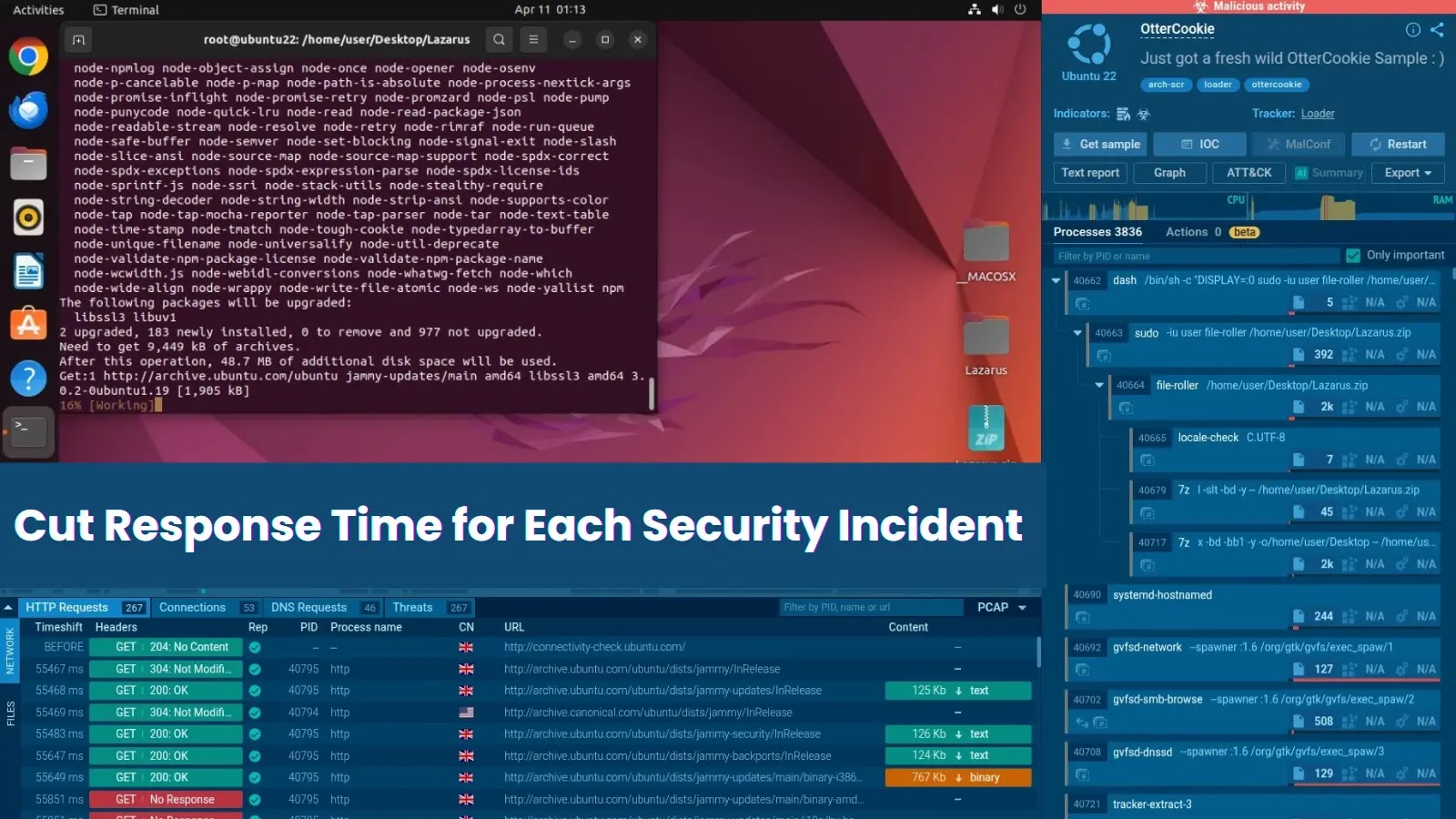
When an incident happens, there’s no time to waste. SOC teams must react fast to protect their organization, and this…
Cloudflare has published a detailed post-mortem explaining the significant outage on September 12, 2025, that made its dashboard and APIs…
The infamous Everest ransomware group has reportedly included Bayerische Motoren Werke AG (BMW) as a high-profile target, claiming the theft…
SquareX first discovered and disclosed Last Mile Reassembly attacks at DEF CON 32 last year, warning the security community of…
A zero-click vulnerability discovered in ChatGPT’s Deep Research agent allowed attackers to exfiltrate sensitive data from a user’s Gmail account…
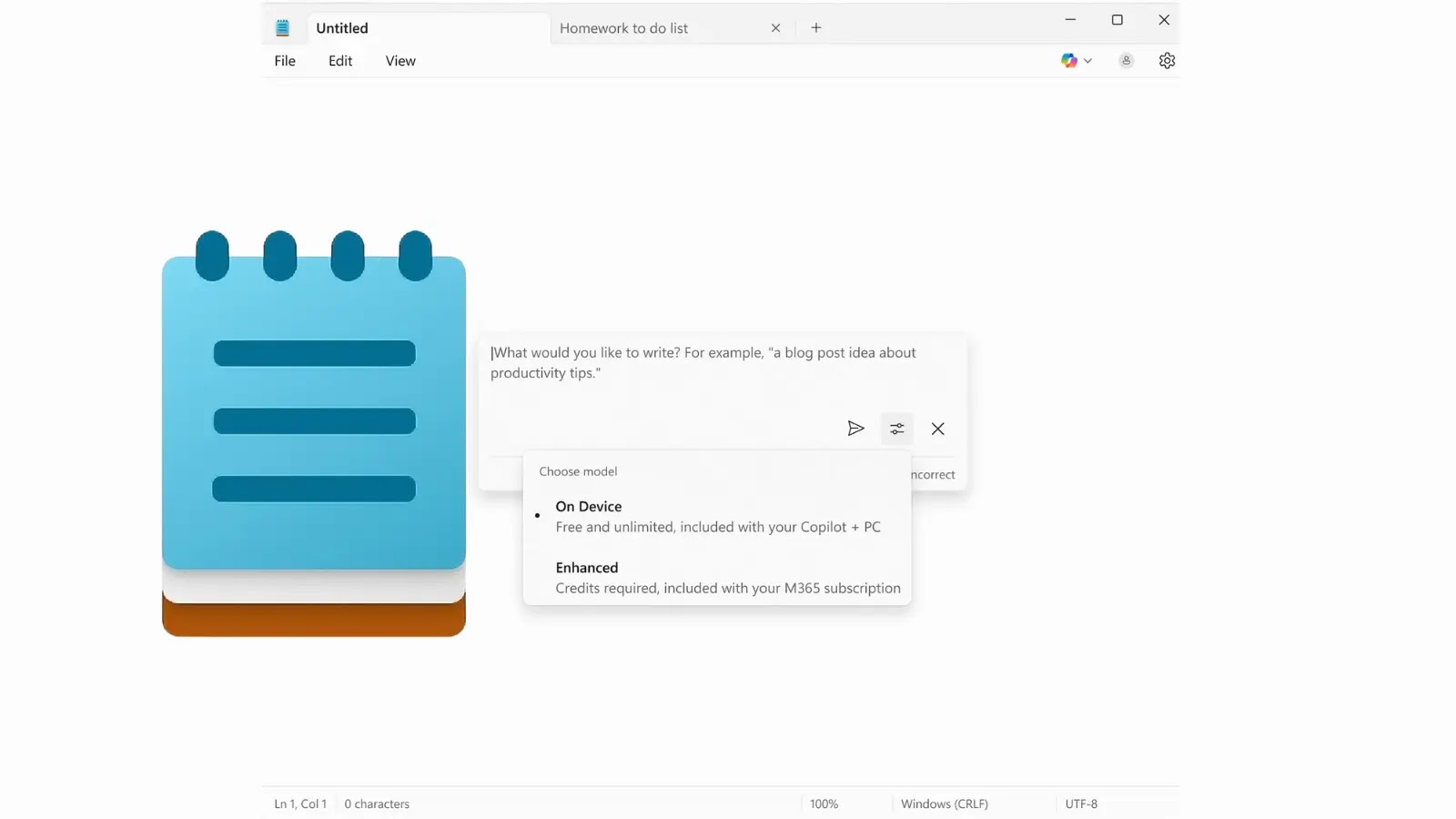
Microsoft is integrating free, on-device artificial intelligence capabilities into the classic Notepad application for Windows 11 users with Copilot+ PCs….
Attackers injected malicious code into GitHub Actions workflows in a widespread campaign to steal Python Package Index (PyPI) publishing tokens….
A critical vulnerability in Microsoft’s Entra ID could have allowed an attacker to gain complete administrative control over any tenant…
Emerging in mid-2025, the shinysp1d3r ransomware-as-a-service (RaaS) platform represents the next evolution of cloud-focused extortion tools. Unlike traditional ransomware that…