Category: CyberSecurityNews
Cary, United States, August 11th, 2025, CyberNewsWire Hands-on cybersecurity and IT training leader recognized for innovation in practical, work-ready education…
A critical zero-day vulnerability has been identified in WinRAR that cybercriminals are actively exploiting through sophisticated phishing campaigns to distribute…
Researchers have compromised OpenAI’s latest GPT-5 model using sophisticated echo chamber and storytelling attack vectors, revealing critical vulnerabilities in the…
A newly disclosed security vulnerability in the popular 7-Zip file compression software has raised significant concerns in the cybersecurity community….
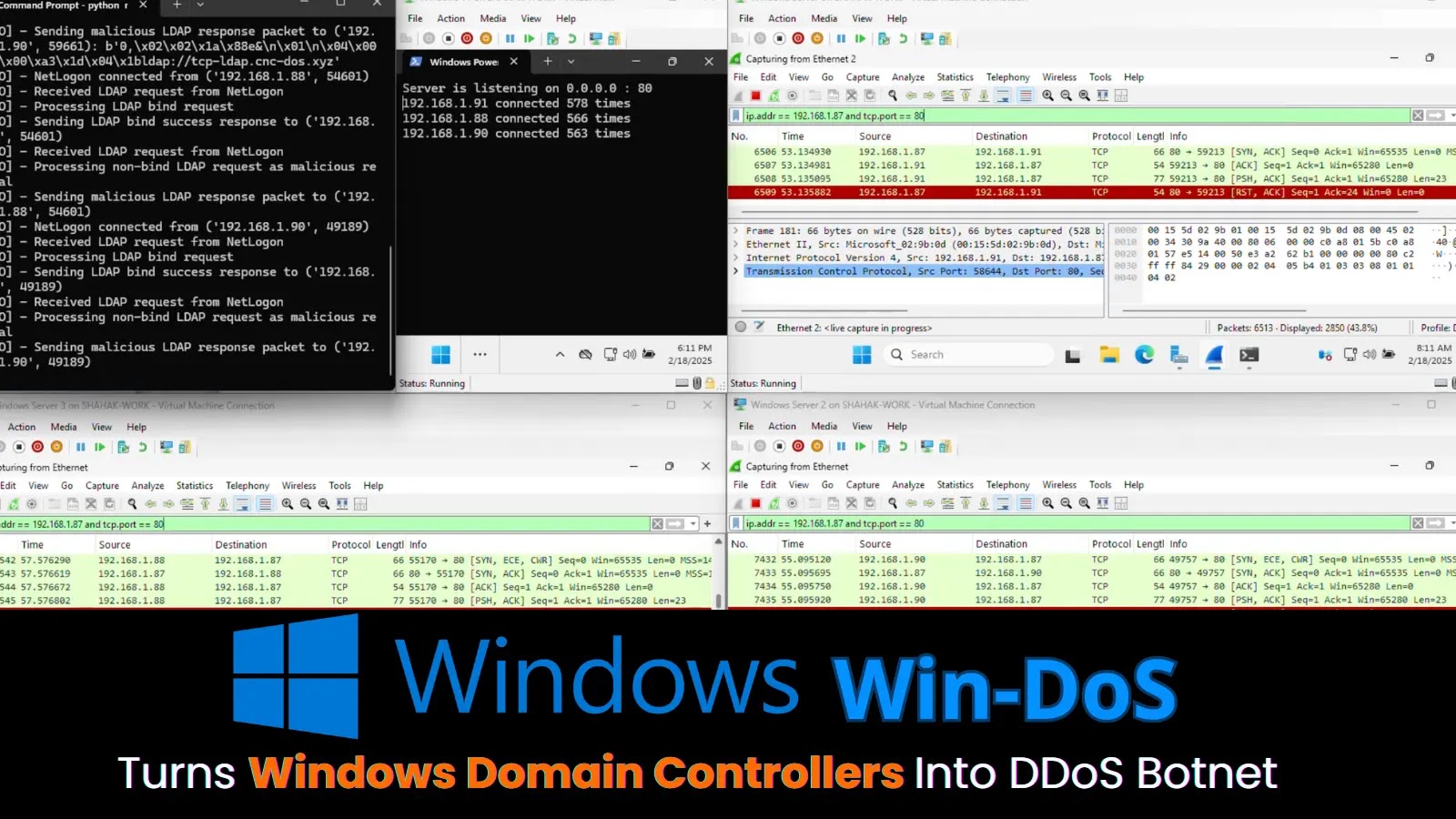
LAS VEGAS — At the DEF CON 33 security conference, researchers Yair and Shahak Morag of SafeBreach Labs unveiled a…
Tech giant Google has officially acknowledged a significant data breach affecting its corporate Salesforce database, with the company completing email…
Darknet markets, operating beyond the reach of traditional payment processors and legal systems, rely on escrow systems to secure cryptocurrency…
Darknet markets, operating beyond the reach of traditional payment processors and legal systems, rely on escrow systems to secure cryptocurrency…
A critical vulnerability in OpenAI’s ChatGPT Connectors feature allows attackers to exfiltrate sensitive data from connected Google Drive accounts without…
August 9, 2025 — A critical vulnerability in the Linux kernel, identified as CVE-2025-38236, has exposed a flaw that could…
A sophisticated cybercriminal enterprise operating over 5,000 fraudulent online pharmacy websites has been exposed in a comprehensive investigation, revealing one…
A sophisticated cryptocurrency theft campaign has emerged targeting the Bittensor ecosystem through malicious Python packages distributed via the Python Package…