Category: CyberSecurityNews
SSL certificates are used everywhere from websites and APIs to mobile apps, internal tools and CI/CD pipelines. While most teams…
A critical vulnerability in Cursor IDE, the rapidly growing AI-powered development environment, enables persistent remote code execution through manipulation of…
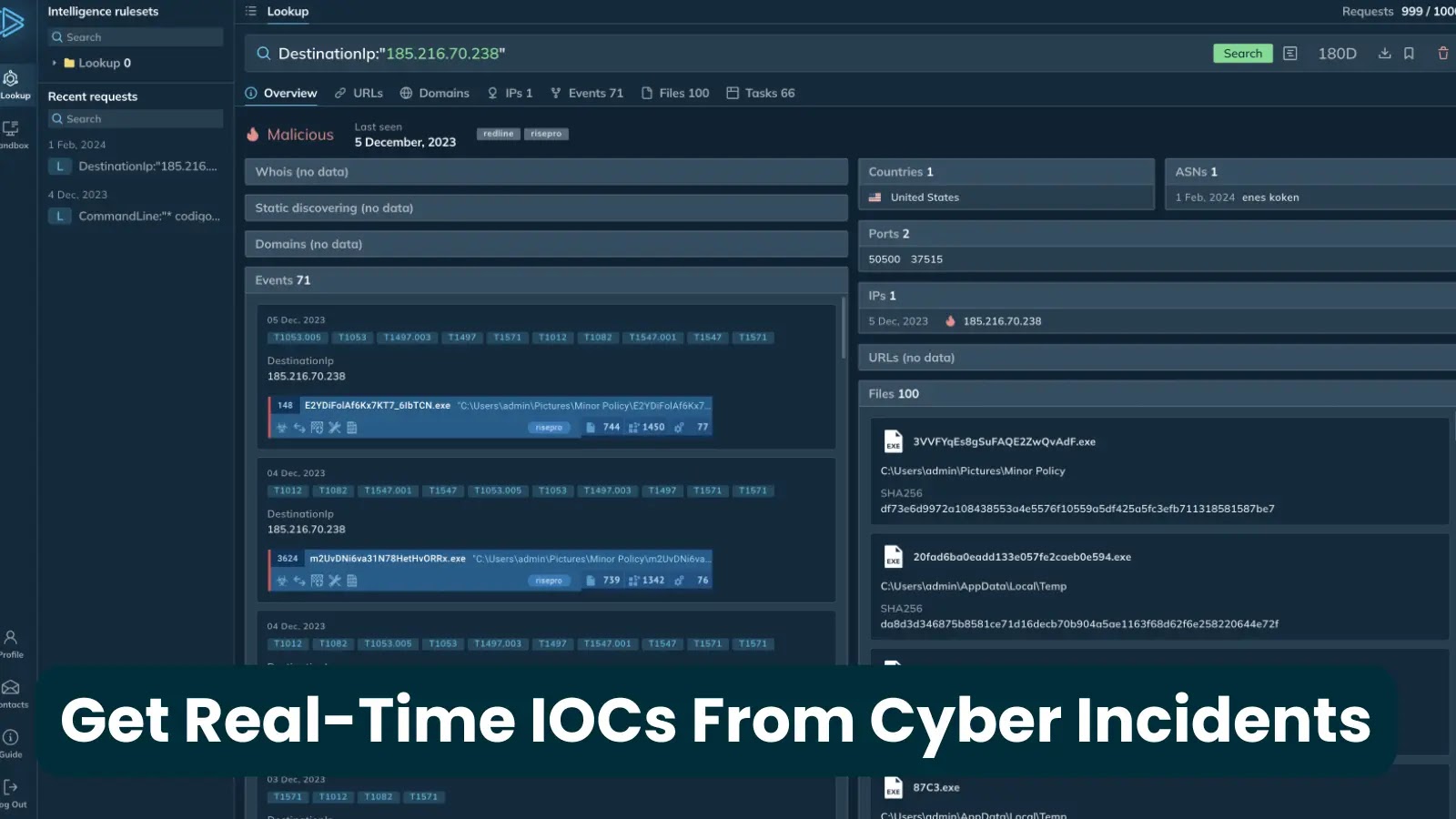
Cybersecurity is about staying one step ahead. The security of business assets hinges on proactive threat detection and rapid response…
SonicWall has issued an urgent security advisory following a significant increase in cyber incidents targeting its Gen 7 SonicWall firewalls…
A critical vulnerability in Streamlit, the popular open-source framework for building data applications, enables attackers to conduct cloud account takeover…
Perplexity AI, an emerging question-answering engine powered by advanced large language models, has recently come under scrutiny for deploying stealth…
A sophisticated phishing campaign attributed to the Pakistan-linked APT36 group has emerged as a serious threat to Indian government infrastructure….
Cisco has confirmed it was the target of a cyberattack where a malicious actor successfully stole the basic profile information…
A sophisticated North Korean cryptocurrency theft campaign has resurfaced with renewed vigor, weaponizing twelve malicious NPM packages to target developers…
North Korean state-sponsored cyber-espionage group Kimsuky has unveiled a sophisticated new campaign targeting South Korean entities through malicious Windows shortcut…
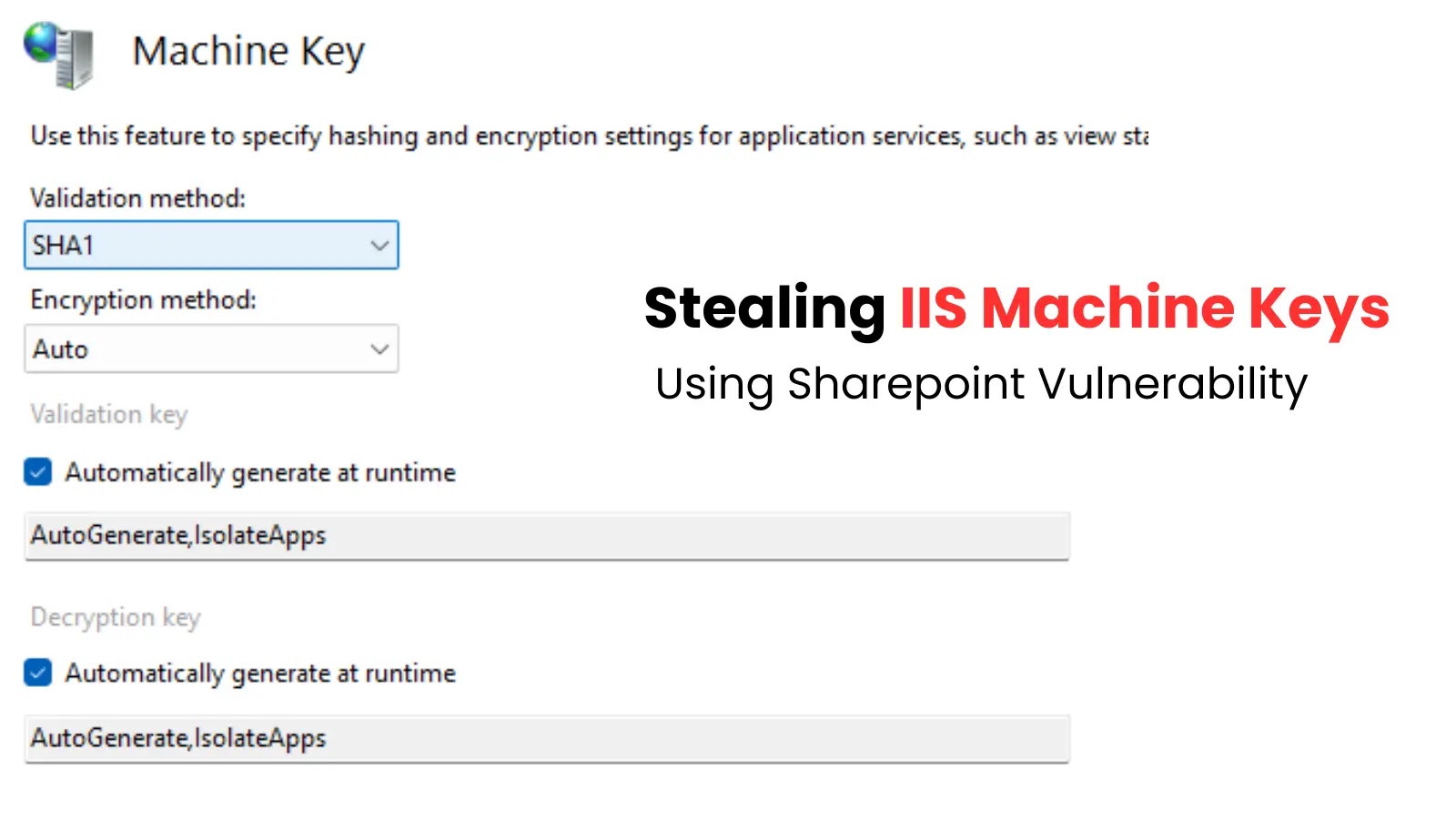
A sophisticated attack method where hackers are exploiting a deserialization vulnerability in SharePoint to steal Internet Information Services (IIS) Machine…
The open-source software ecosystem, once considered a bastion of collaborative development, has become an increasingly attractive target for cybercriminals seeking…