Category: CyberSecurityNews
A severe security vulnerability has been discovered in the widely-used Insomnia API Client that allows attackers to execute arbitrary code…
A sophisticated malware campaign targeting ComfyUI, a popular AI image generation framework, has successfully compromised at least 695 servers worldwide,…
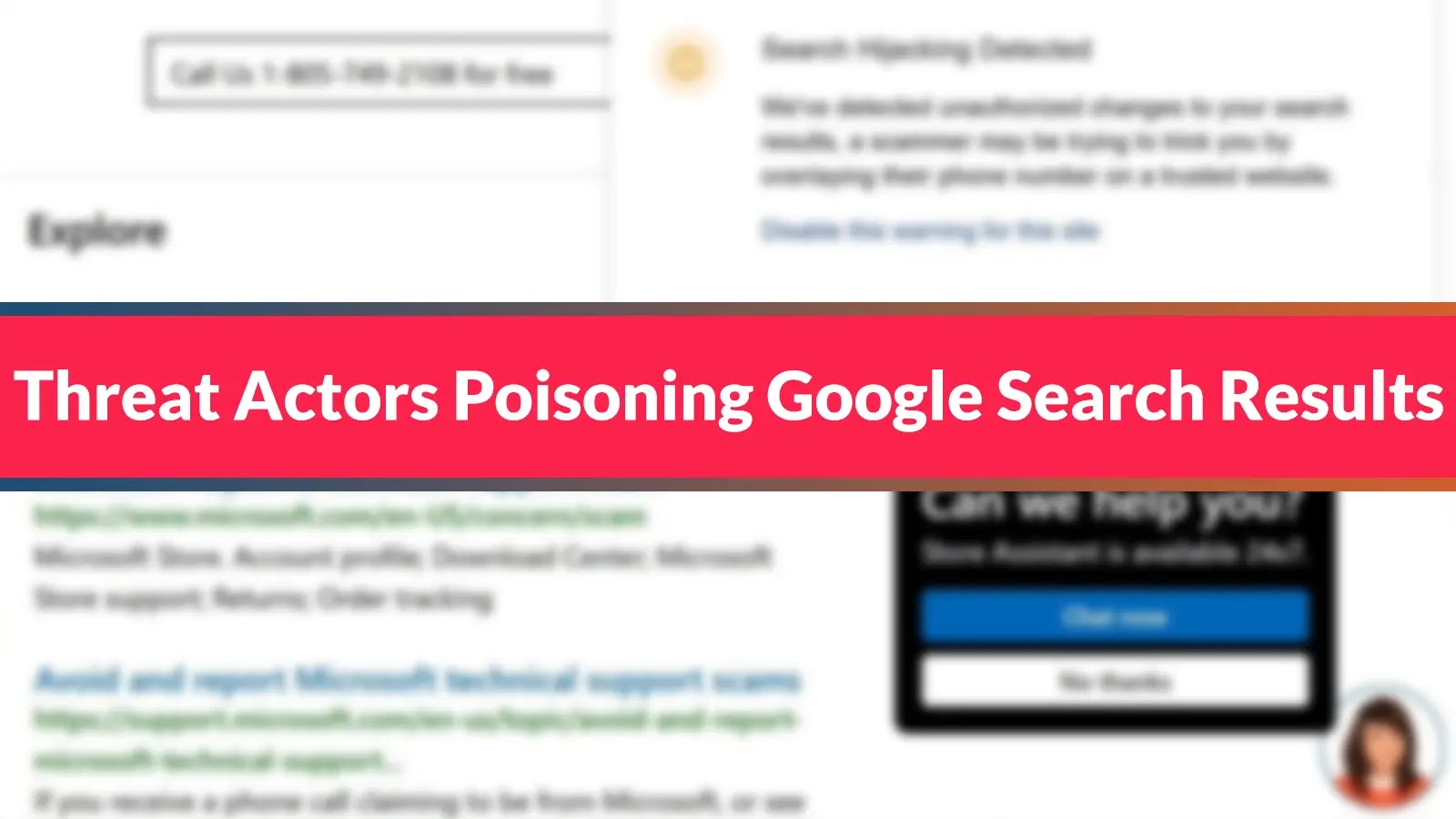
In a concerning development for internet users, cybercriminals have devised a sophisticated new technique to manipulate Google search results, effectively…
A sophisticated new threat actor known as Mocha Manakin has emerged in the cybersecurity landscape, employing an increasingly popular social…
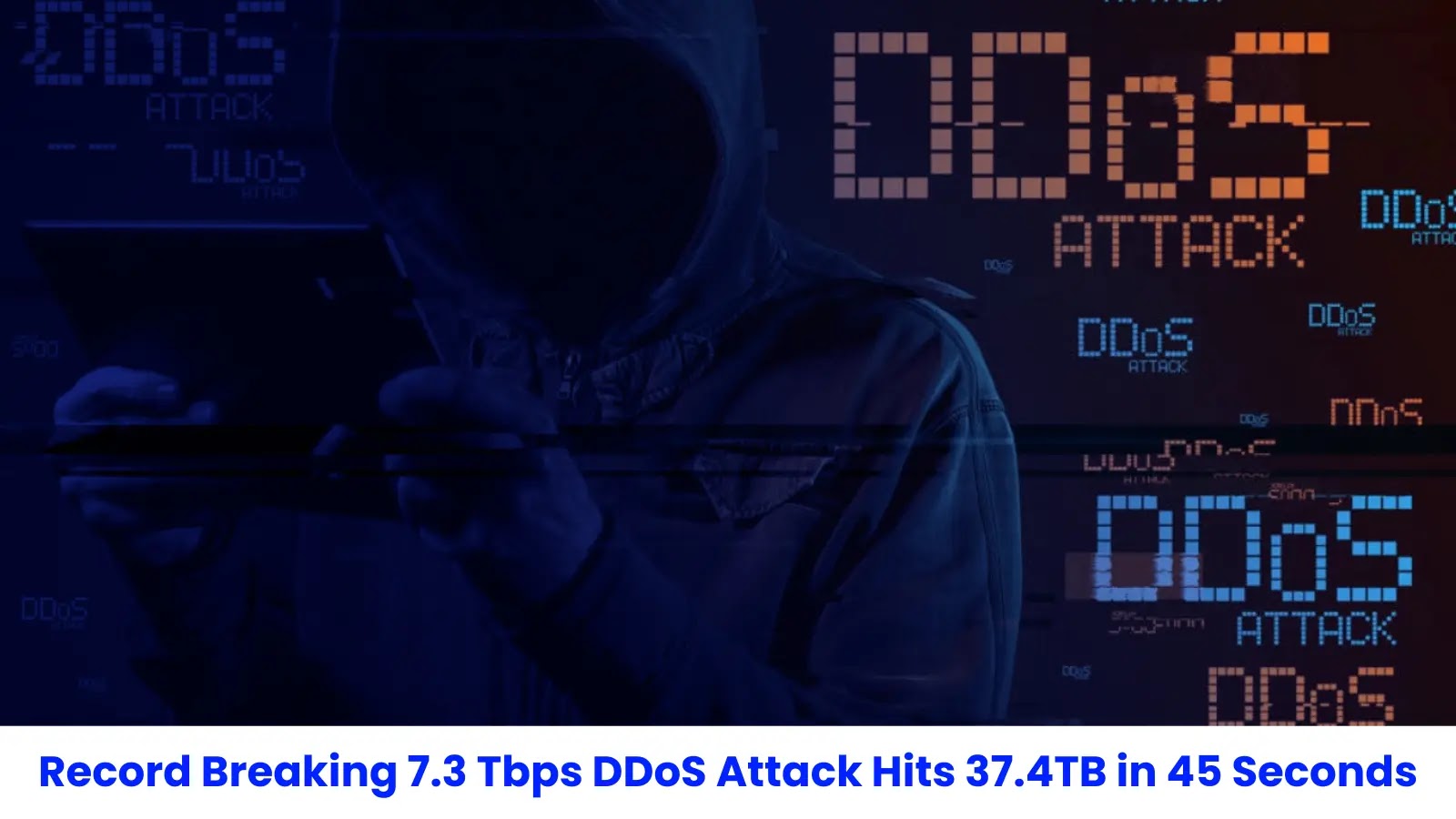
The largest distributed denial-of-service (DDoS) attack ever documented was successfully stopped by Cloudflare in mid-May 2025, with attackers unleashing a…
Cybersecurity professionals across East and Southeast Asia are facing a sophisticated new threat as China-linked attackers deploy a weaponized MSI…
Summary 1. A OneDrive bug is causing some users’ search results to appear blank, though files are still accessible. 2….
Cybersecurity researchers have uncovered a significant resurgence of the Prometei botnet, a sophisticated malware operation targeting Linux servers for cryptocurrency…
Summary 1. Redirection controls disable clipboard, drive, USB, and printer access by default to prevent data exfiltration and malware injection….
Microsoft is expanding the number of passkey authentication methods available in Microsoft Entra ID to improve its identity and access…
A new detection method called Jitter-Trap that turns cybercriminals’ own evasion tactics against them, offering new hope in the battle…
A sophisticated new variant of the Masslogger credential stealer has emerged, utilizing VBScript encoded (.VBE) files to deploy a multi-stage…