Category: CyberSecurityNews
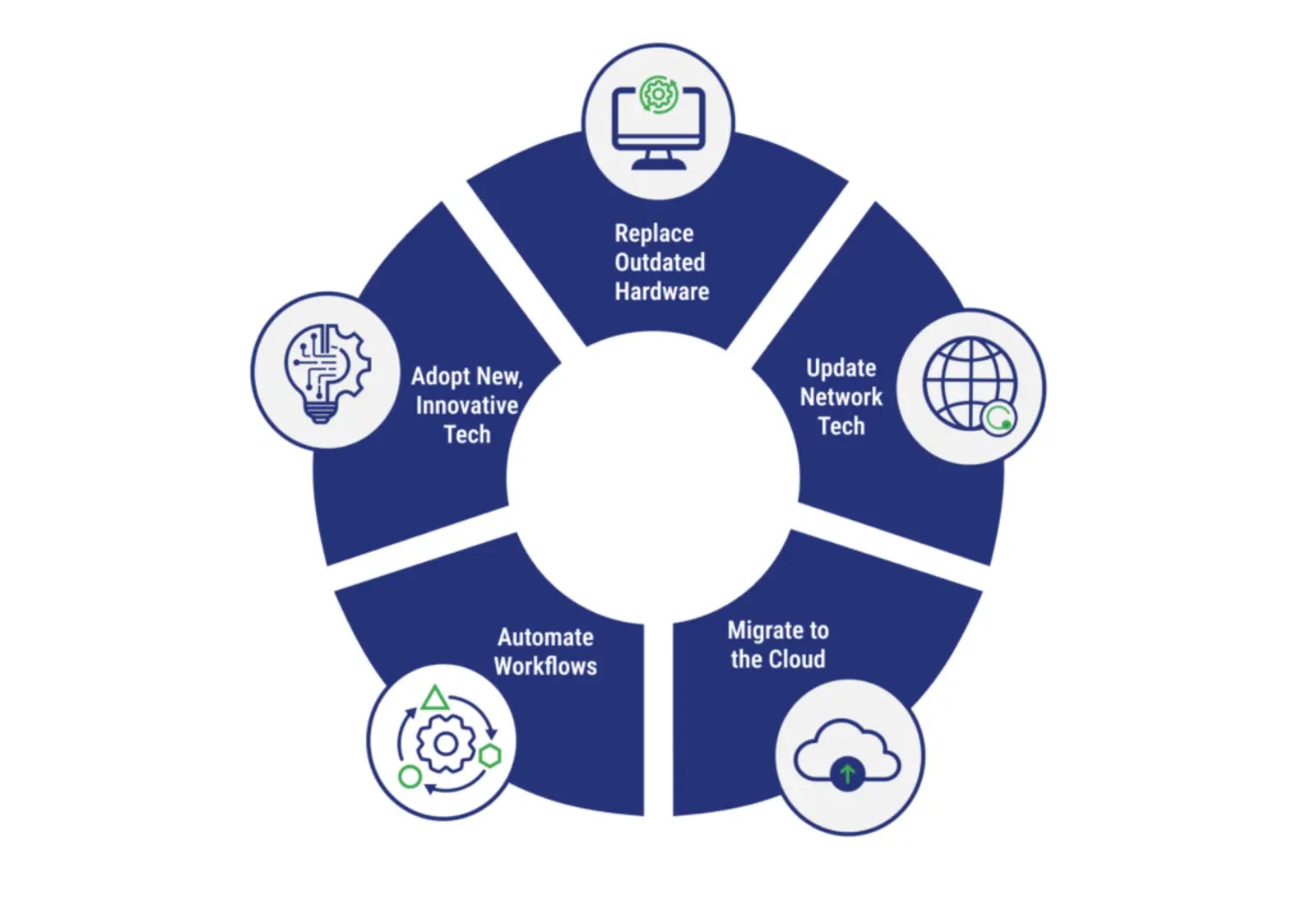
In 2025, modernizing outdated IT infrastructure is key for organizations aiming to stay competitive, secure, and scalable. Finding a reliable…
A massive exposure of Microsoft SharePoint servers to internet-based attacks has been identified, with over 17,000 servers exposed and 840…
Cybersecurity researchers have uncovered more than 10 patents for highly intrusive forensics and data collection technologies filed by Chinese companies…
Google Project Zero has announced a significant shift in its vulnerability disclosure practices, implementing a new trial policy that will…
A critical security vulnerability has been identified in OAuth2-Proxy, a widely-used reverse proxy that provides authentication services for Google, Azure,…
A financially motivated threat group known as UNC2891 orchestrated a sophisticated attack on banking infrastructure by physically installing a 4G-equipped…
A sophisticated cyberattack exploiting a zero-day vulnerability in Microsoft SharePoint servers has compromised over 400 entities globally, with significant impact…
The Bangalore-based software engineer Rahul Agarwal, employee of prominent crypto exchange CoinDCX, was arrested in connection with a massive $44…
The maritime industry, which facilitates approximately 90% of global trade, has emerged as a critical battleground for advanced persistent threat…
A significant zero-day vulnerability in CrushFTP has been disclosed, allowing unauthenticated attackers to achieve complete remote code execution on vulnerable…
Cybersecurity researchers have successfully developed and released a free decryption tool for the FunkSec ransomware, a malicious strain that leveraged…
A sophisticated new Linux variant of Gunra ransomware has emerged, marking a significant escalation in the threat group’s cross-platform capabilities…