Category: CyberSecurityNews
Organizations worldwide are facing an unprecedented surge in sophisticated phishing attacks that specifically target Microsoft 365 and Google accounts through…
Threat actors are allegedly offering the complete source code of a sophisticated Malware-as-a-Service (MaaS) botnet for sale. This advanced malicious…
Multiple critical security vulnerabilities in the Trend Micro Apex One enterprise security platform could enable attackers to inject malicious code and escalate…
A newly disclosed command injection vulnerability in Palo Alto Networks’ PAN-OS operating system poses significant security risks to enterprise firewall…
A critical zero-day vulnerability affecting Windows systems that allows attackers to achieve privilege escalation through a novel Reflective Kerberos Relay…
CISA and international cybersecurity partners have released a comprehensive suite of guidance documents aimed at protecting critical network edge devices…
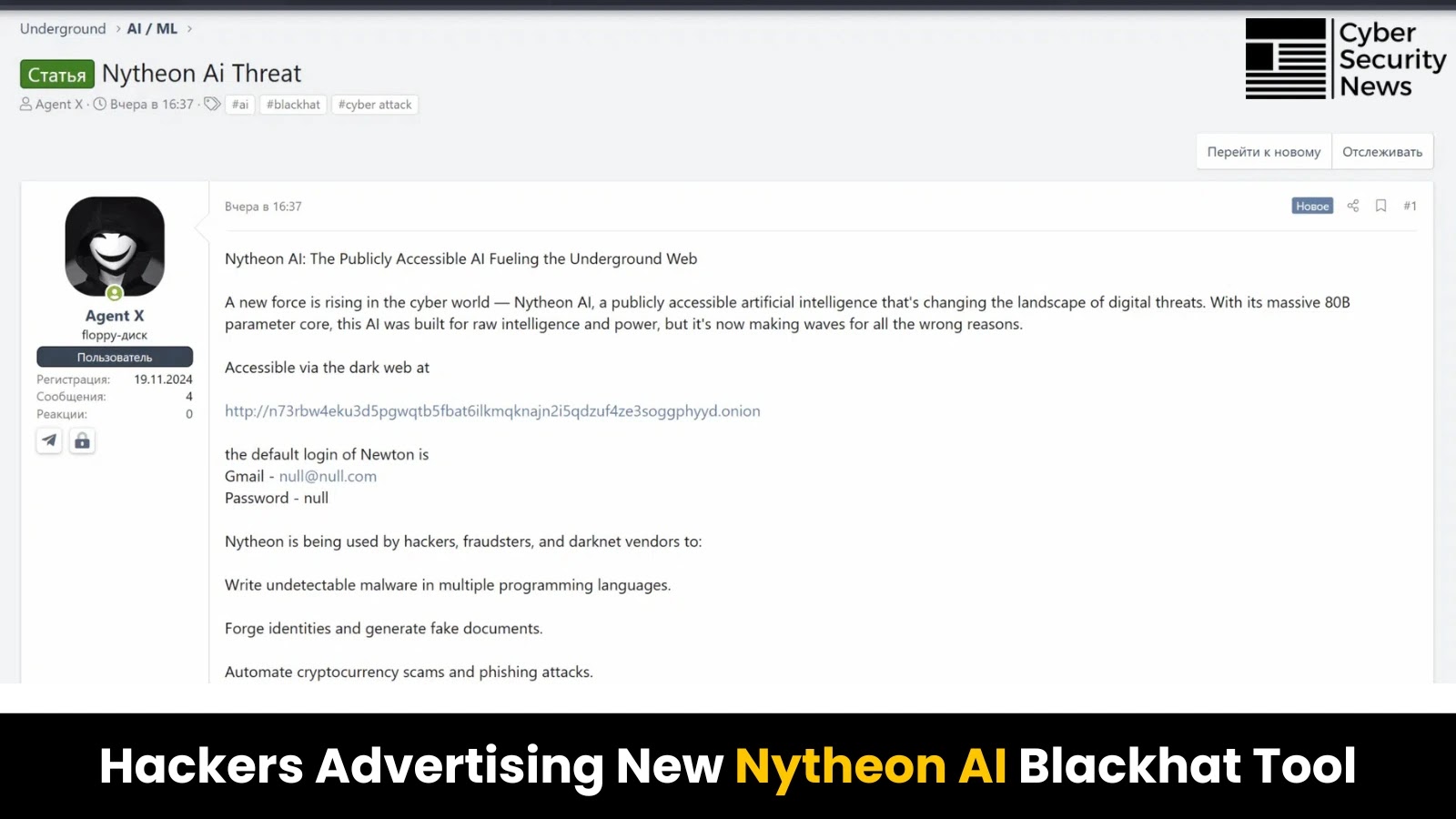
A sophisticated new threat platform, Nytheon AI, has emerged, which combines multiple uncensored large language models (LLMs) built specifically for…
A critical zero-click vulnerability in Microsoft 365 Copilot, dubbed “EchoLeak,” enables attackers to automatically exfiltrate sensitive organizational data without requiring…
The urgency stems from requirements imposed by technology partners, which necessitated an accelerated timeline for implementation across all affected products….
More than 20,000 malicious IP addresses and domains linked to information stealers have been taken down in an INTERPOL-coordinated operation…
Multiple critical vulnerabilities in Microsoft Office could allow attackers to execute arbitrary code on affected systems. The vulnerabilities, tracked as…
A critical security vulnerability in the Windows Common Log File System Driver (CLFS) enables attackers to escalate their privileges to…