Category: CyberSecurityNews
As organizations increasingly adopt multi-cloud environments to leverage flexibility, scalability, and cost-efficiency, securing these complex infrastructures has become a top…
Generative artificial intelligence (GenAI) has emerged as a transformative force across industries, enabling content creation, data analysis, and decision-making breakthroughs….
Security researchers uncovered critical zero-day vulnerabilities across major enterprise platforms during the second day of Pwn2Own Berlin 2025, earning a…
North Korean state-sponsored threat actor APT Group 123 has intensified its cyber espionage campaign, specifically targeting Windows systems across multiple…
In April 2025, cybersecurity teams were starkly reminded of the stakes involved in patch management when Microsoft disclosed CVE-2025-29824, a zero-day…
Critical security flaws have been uncovered in Ivanti Endpoint Manager Mobile (EPMM), a widely used mobile device management (MDM) solution,…
The Federal Bureau of Investigation (FBI) issued an urgent warning Thursday about an ongoing malicious campaign where cybercriminals are impersonating…
In a significant setback for US cybercrime enforcement efforts, Russian hacker Andrei Tarasov has evaded extradition to the United States…
A recent investigation has uncovered a concerning case of espionage at one of America’s premier academic institutions, where a Chinese…
A newly discovered class of vulnerabilities in Intel processors, termed Branch Predictor Race Conditions (BPRC), allows attackers to systematically extract…
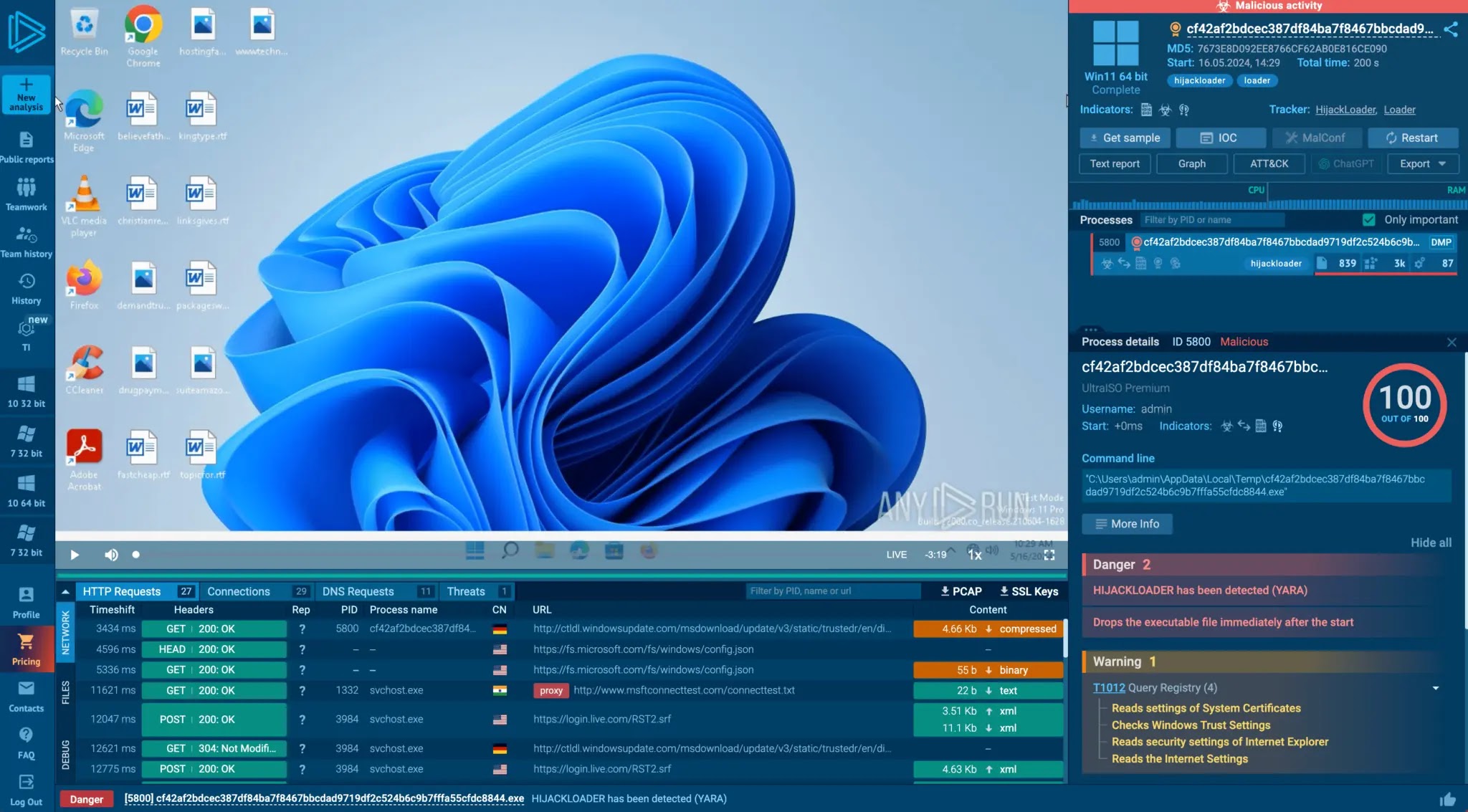
Security Operations Centers (SOCs) and Managed Security Service Providers (MSSPs) operate at the forefront of cybersecurity, tasked with defending organizations…
Apple’s macOS Gatekeeper, a cornerstone of the operating system’s defense against malicious software, has undergone significant macOS Sequoia (15.0) updates…