Category: CyberSecurityNews
Cybersecurity researchers have uncovered a sophisticated technique to bypass Microsoft’s phishing-resistant multi-factor authentication (MFA) by exploiting the device code authentication…
In a sophisticated business email compromise (BEC) scheme, cybercriminals are targeting tenants with fraudulent requests to redirect rent payments to…
A sophisticated malware variant masquerading as a legitimate WordPress security plugin has been identified, capable of providing attackers with persistent…
In today’s hyper-connected business environment, supply chains are no longer just about the physical movement of goods they are digital…
In 2025, with cybersecurity threats evolving at an unprecedented pace, effective patch management has never been more critical for organizational…
The multi-cloud landscape has transformed enterprise IT, with over 87% of organizations now operating across multiple cloud platforms. This distributed…
Security experts revealed a critical vulnerability in Ruby on Rails that allows attackers to bypass Cross-Site Request Forgery (CSRF) protections….
A critical security flaw in Oracle VM VirtualBox (CVE-2024-21113) has been patched after researchers discovered it could allow local attackers…
In today’s fast-paced digital landscape, CISOs play a pivotal role in organizational success, navigating the critical balance of innovation vs…
SonicWall has issued an urgent warning to customers that threat actors are actively exploiting a high-severity command injection vulnerability in…
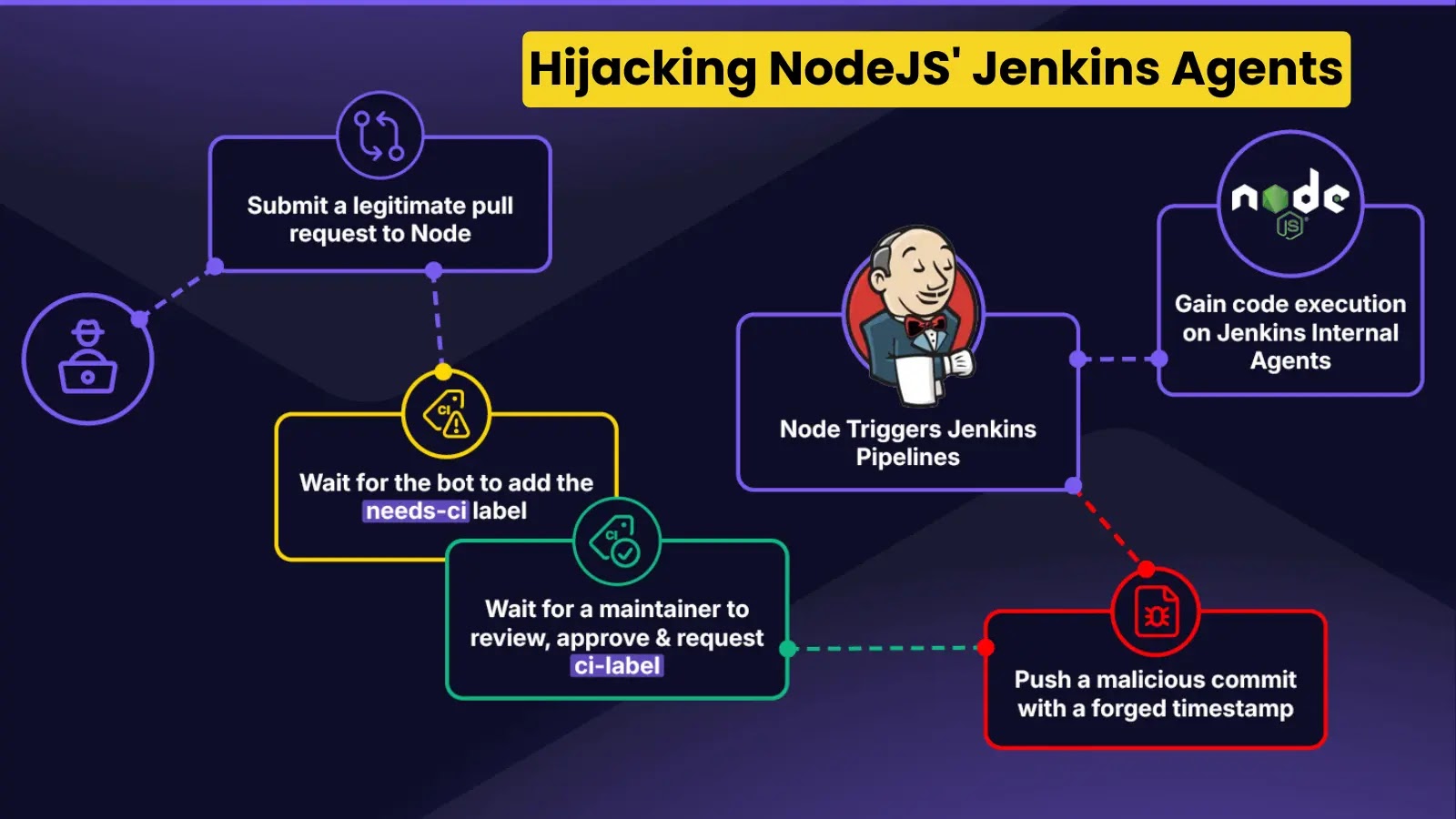
Security researchers recently uncovered a critical vulnerability in Node.js’s continuous integration infrastructure that allowed attackers to execute malicious code on…
A security researcher identified as Remy disclosed a critical vulnerability discovered during a YesWeHack bug bounty engagement. The researcher uncovered…