Category: CyberSecurityNews
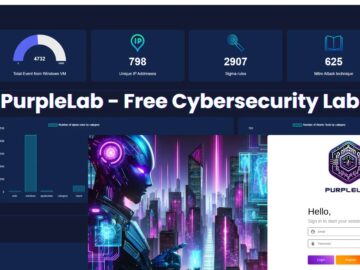
In a significant step forward for cybersecurity professionals, PurpleLab offers an innovative open-source cybersecurity lab for creating and testing detection…
Threat actors have been utilizing a modified version of the SharpHide tool to create hidden registry values, significantly complicating detection…
In a sophisticated cyberattack campaign, a threat actor identified as Storm-2372 has been leveraging Microsoft Teams meeting invites to execute…
In a significant update, Google has announced that its AI-powered security feature is now available to every Chrome user globally….
Linus Torvalds has released Linux Kernel 6.14-rc3, the latest release candidate for the upcoming Linux 6.14 stable version. Paolo Bonzini,…
Cyber threats have evolved significantly in recent years, with malicious actors employing sophisticated tactics to compromise user systems. One such…
North Korean IT workers have been infiltrating international companies by securing remote positions under false identities. This tactic not only…
The notorious Lazarus Group in a recent escalation of cyber threats linked to North Korea, has unveiled a sophisticated new…
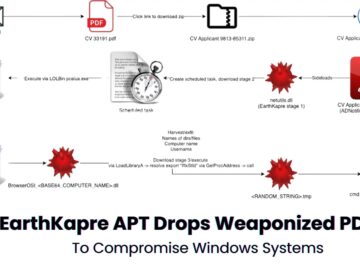
A highly sophisticated cyber espionage group known as EarthKapre, also referred to as RedCurl, has been identified targeting private-sector organizations,…
Job seekers have become the target of a sophisticated ransomware campaign in a recent cybersecurity threat, and this campaign dubbed…
The notorious Lazarus Group, a North Korean Advanced Persistent Threat (APT) group, has been linked to a sophisticated campaign targeting…
A website launched by Elon Musk’s Department of Government Efficiency (DOGE) has been found to have a significant security vulnerability,…