Category: CyberSecurityNews
A recently discovered Python script has been flagged as a potential cybersecurity threat due to its use of a clever…
Researchers have identified a new backdoor malware, written in Go programming language, that leverages Telegram as its command-and-control (C2) channel….
A critical authentication bypass vulnerability in SonicWall firewalls, tracked as CVE-2024-53704, is now being actively exploited in the wild, cybersecurity…
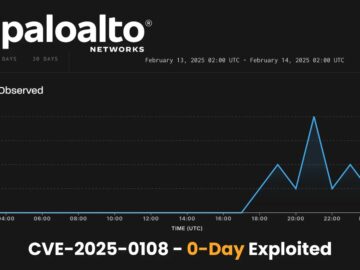
Palo Alto Networks has released a patch for a high-severity authentication bypass vulnerability, identified as CVE-2025-0108, affecting their PAN-OS software. GreyNoise…
A newly disclosed high-severity vulnerability in WinZip, tracked as CVE-2025-1240, enables remote attackers to execute arbitrary code on affected systems…
A sophisticated phishing campaign, identified by Microsoft Threat Intelligence, has been exploiting a technique known as “device code phishing” to…
Researchers have uncovered a high-severity SQL injection vulnerability, CVE-2025-1094, affecting PostgreSQL’s interactive terminal tool, psql. This flaw was identified during…
Researchers observed a sophisticated cyber-espionage campaign led by the Chinese state-sponsored group known as “Salt Typhoon,” also referred to as…
A high-severity security vulnerability, identified as CVE-2024-21966, has been discovered in the AMD Ryzen™ Master Utility, a software tool designed…
Progress has disclosed multiple critical security vulnerabilities affecting its LoadMaster product line, including the Multi-Tenant (MT) hypervisor. These vulnerabilities, identified…
Discord has introduced a groundbreaking privacy feature called “Ignore.” This announcement coincides with Safer Internet Day 2025, celebrated globally on…
SAP has released 19 new Security Notes and two updates to existing patches in its February 2025 Security Patch Day,…