Category: CyberSecurityNews
Zoom, the popular video conferencing platform, has addressed several vulnerabilities across its suite of applications, ranging from privilege escalation to…
Cisco has released security vulnerabilities impacting its ThousandEyes Endpoint Agent for macOS and RoomOS, as well as its Snort detection…
The Cybersecurity and Infrastructure Security Agency (CISA) has unveiled the AI Cybersecurity Collaboration Playbook, a new guidance document aimed at…
Microsoft has disclosed a newly identified critical security vulnerability (CVE-2025-21298) affecting Object Linking and Embedding (OLE), a technology widely used…
The Cybersecurity and Infrastructure Security Agency (CISA) has recently updated its Known Exploited Vulnerabilities (KEV) catalog to include critical zero-day…
Fortinet has released a security update with the fixes for 15 vulnerabilities that affect multiple products with distinct security issues,…
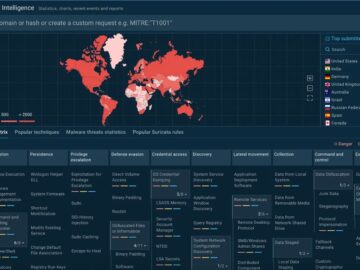
Effective cyber threat detection and response depend on the ability to access actionable, real-time intelligence. ANY.RUN, a trusted name in…
SAP has disclosed two critical vulnerabilities in its NetWeaver Application Server for ABAP and ABAP Platform, urging immediate action to…
The Open Worldwide Application Security Project’s (OWASP) released the first “Non-Human Identities (NHI) Top 10 used to provide authorization to…
Cybersecurity researchers at EXPMON have uncovered an intriguing “zero-day behavior” in PDF samples that could potentially be exploited by attackers…
A critical vulnerability in Google’s “Sign in with Google” authentication flow is putting millions of Americans at risk of data…
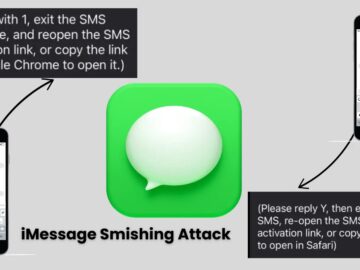
A new smishing (SMS phishing) campaign is making waves, specifically targeting iMessage users by manipulating Apple’s built-in phishing protections. Users…