Category: CyberSecurityNews
Researchers discovered five malicious npm packages that target Roblox developers, spreading malware to steal credentials and personal information. These packages,…
Hackers weaponize Excel documents primarily due to their widespread use and the inherent vulnerabilities within the software. With Microsoft blocking…
Decentralized finance (DeFi) protocol DeltaPrime has fallen victim to yet another major exploit. Hackers siphoned off approximately $4.8 million worth of ARB and AVAX tokens. The…
A newly disclosed security vulnerability, CVE-2024-47295, has been found in several Epson devices, including printers, scanners, and network interface products….
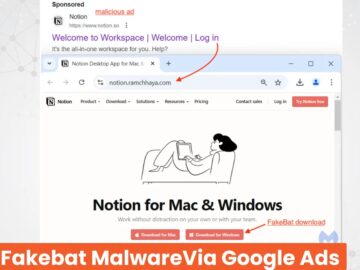
Cybersecurity researchers have uncovered a resurgence of the Fakebat malware loader being distributed through malicious Google Ads. After a months-long…
Palo Alto Networks has issued an urgent warning about a potential critical remote code execution (RCE) vulnerability affecting the management…
A critical security flaw in Microsoft Bookings has been uncovered. This flaw, inherent in the default configuration of Microsoft Bookings,…
Threat actors are actively exploiting a critical vulnerability in Veeam Backup & Replication software to deploy a new ransomware strain…
Welcome to this week’s Cybersecurity Newsletter, where you’ll find the latest updates and insights from the world of cybersecurity. Stay…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued urgent warnings regarding two critical vulnerabilities currently being exploited in the…
ESET’s recent report details the activities of various advanced persistent threat (APT) groups from April to September 2024, highlighting key…
Cybercriminals have launched a large-scale phishing attack using a new variant of Rhadamanthys Stealer, dubbed CopyRh(ight)adamantys, which targets individuals and…