Category: CyberSecurityNews
A new vulnerability has been discovered in Telegram, allowing a threat actor to hijack a Telegram user session via XSS…
In a sophisticated cyberattack that unfolded over 29 days, cybersecurity analysts have meticulously traced the steps of threat actors from…
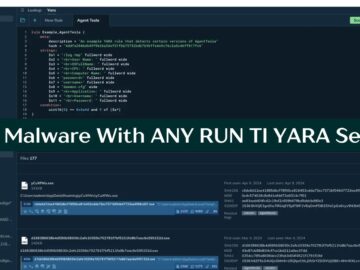
YARA is a rule-based malware detection tool that utilizes regular expressions and textual/binary signatures to create descriptions (rules) for identifying…
Researchers discovered a vulnerability in an archived Apache project, highlighting the risk of using outdated third-party dependencies, where attackers can…
Autodesk Drive is a data-sharing platform for organizations to share documents and files in the cloud. It also supports 2D…
The Cactus ransomware gang has been exploiting vulnerable Qlik sense servers ever since November 2023 using multiple vulnerabilities such as…
Google announced the release of Chrome 124, which fixes four vulnerabilities, including a critical security issue that allows attackers to execute…
In a significant move for tech enthusiasts and historians alike, Microsoft has made the source code for MS-DOS 4.0 publicly…
The Iranian state-sponsored threat actor MuddyWater has been observed exploiting a legitimate remote monitoring and management (RMM) tool, Atera Agent,…
Hackers often target WordPress plugins as they have security loopholes that they can exploit to hack into sites without permission. …
Progress addressed a critical vulnerability last week, which was associated with an unauthenticated Command injection on the Progress Flowmon product….
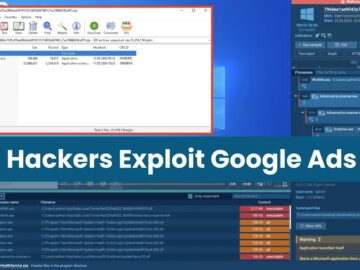
Malicious actors are distributing a new backdoor, MadMxShell, through a Google Ads campaign that impersonates an IP scanner. This Windows…