Category: GBHackers
Frankfurt am Main, Germany, September 9th, 2025, CyberNewsWire The threat landscape surrounding distributed denial-of-service (DDoS) attacks intensified significantly in the…
South Korean internet users are being targeted by a sophisticated phishing campaign attributed to the North Korean threat actor known…
Silver Spring, USA, September 9th, 2025, CyberNewsWire Fast Company today announced its seventh-annual Best Workplaces for Innovators list, recognizing businesses that foster a…
In a sweeping effort to curb transnational cybercrime and human rights abuses, the U.S. Department of the Treasury’s Office of…
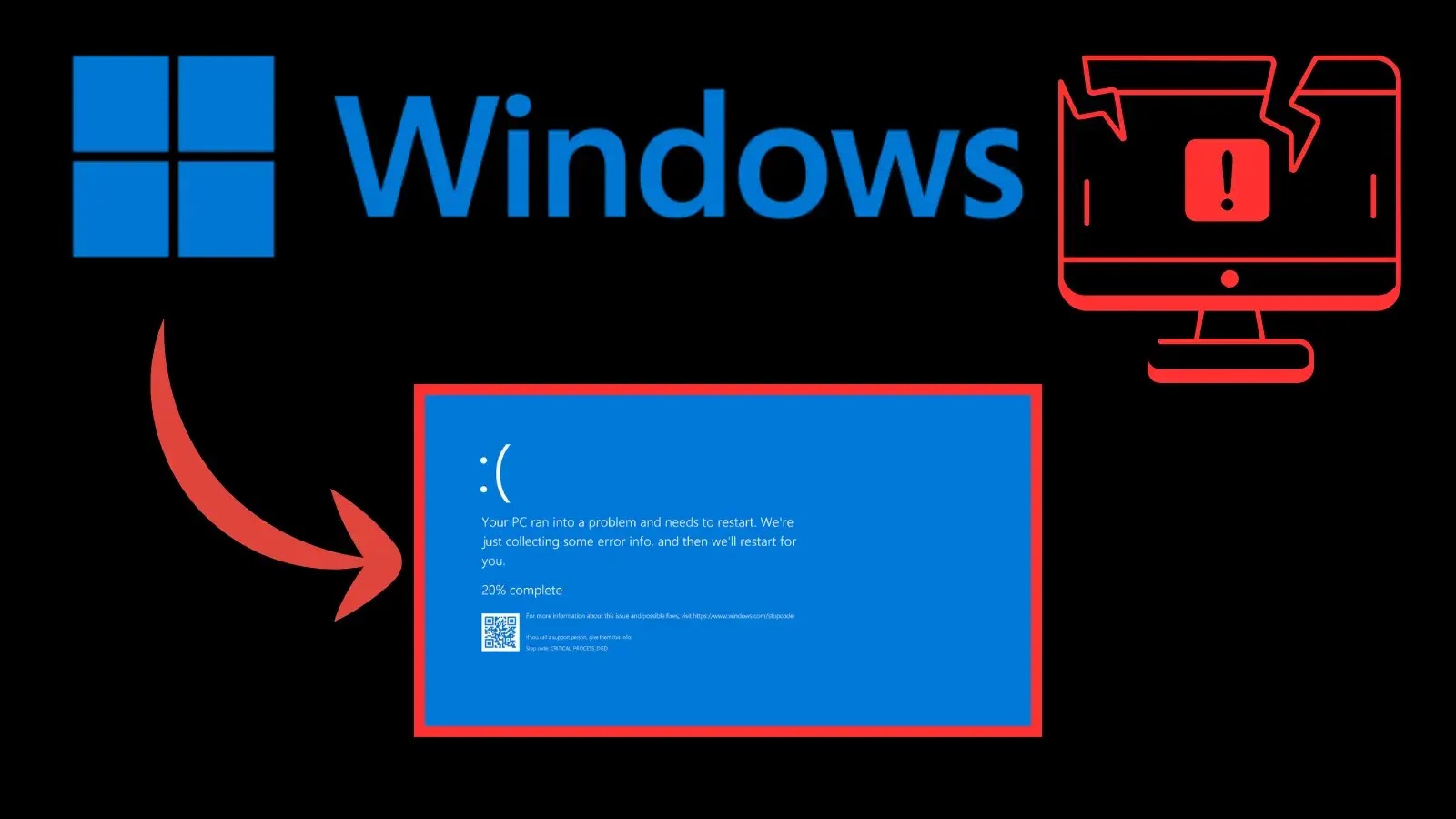
Windows devices rely on a complex ecosystem of drivers to manage hardware and software interactions. When one driver fails to…
An emerging threat campaign has been identified that weaponizes a trojanized version of DeskSoft’s EarthTime application to deploy sophisticated malware,…
SAP’s Security Patch Day on September 9, 2025, introduced fixes for 21 newly discovered vulnerabilities across its product portfolio and…
Jaguar Land Rover’s UK factories will remain closed until at least Wednesday as the company continues to recover from a…
The Akamai Hunt Team has uncovered a new strain of malware that targets exposed Docker APIs with expanded infection capabilities….
Cybersecurity researchers at FortiGuard Labs have uncovered a sophisticated phishing campaign that deploys the MostereRAT remote access trojan to compromise…
The North Korean-aligned threat group APT37, also known as ScarCruft, Ruby Sleet, and Velvet Chollima, has evolved its cyber warfare…
Cybersecurity researchers at Silent Push have uncovered a sophisticated Chinese espionage operation linking two prominent threat actors, Salt Typhoon and…