Category: GBHackers
Armis Labs has uncovered ten critical security flaws collectively named “Frostbyte10” in Copeland’s E2 and E3 building management controllers. These…
Security teams have issued a warning after Google researchers detected active attacks exploiting a new zero-day vulnerability in Sitecore products….
The Django development team has issued security updates after discovering a high-severity SQL injection flaw in the FilteredRelation feature. This flaw could…
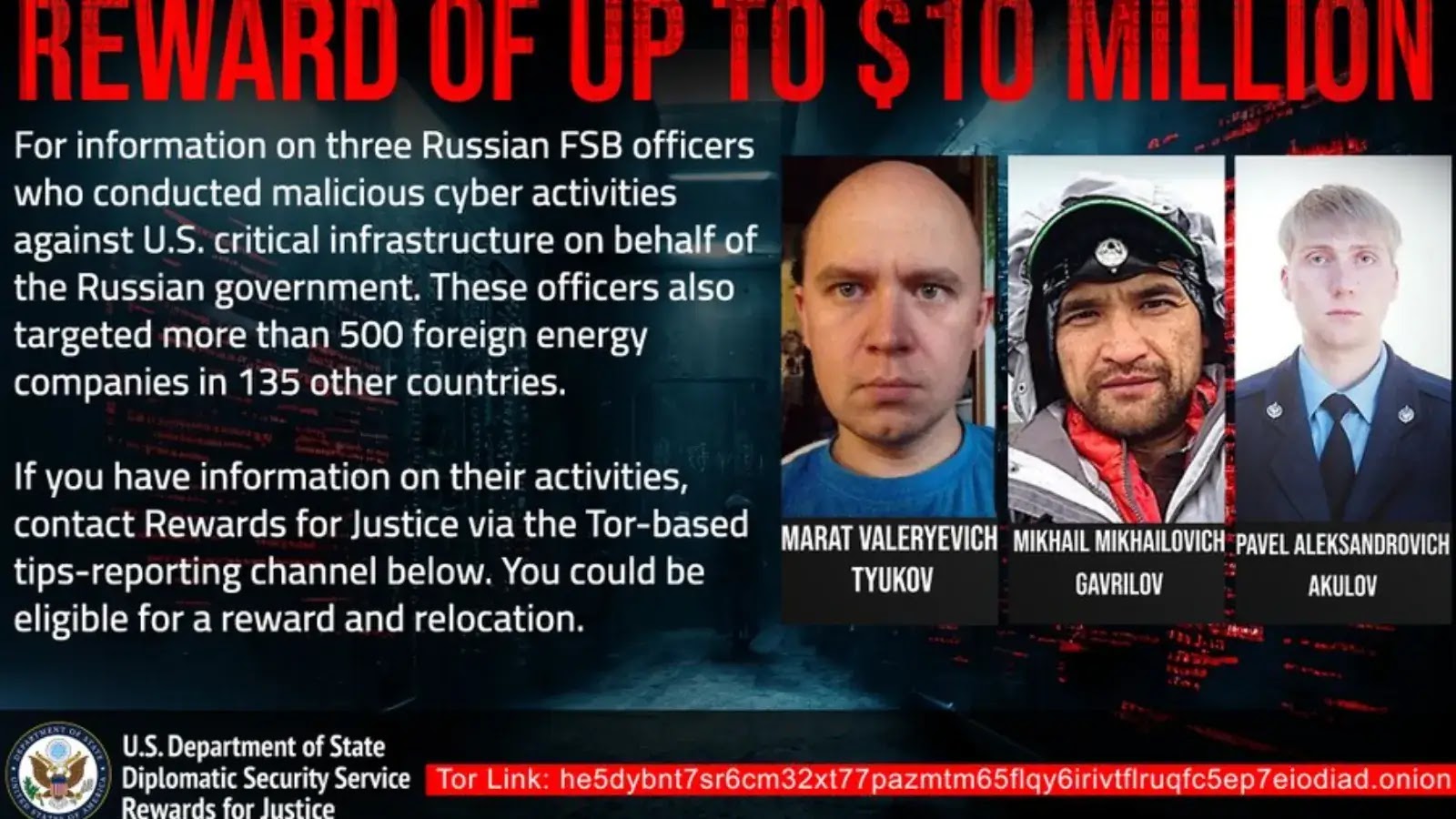
The U.S. government has unveiled a $10 million reward for information leading to the arrest of three Russian FSB officers….
Chinese state-sponsored Advanced Persistent Threat (APT) groups have escalated their cyber espionage campaigns, systematically targeting global telecommunications, government, and military…
Cybersecurity firm Silent Push has exposed a colossal illegal Internet Protocol Television (IPTV) network, revealing a sophisticated piracy operation that…
A highly sophisticated phishing campaign is targeting PayPal users with a deceptive email designed to grant scammers direct access to…
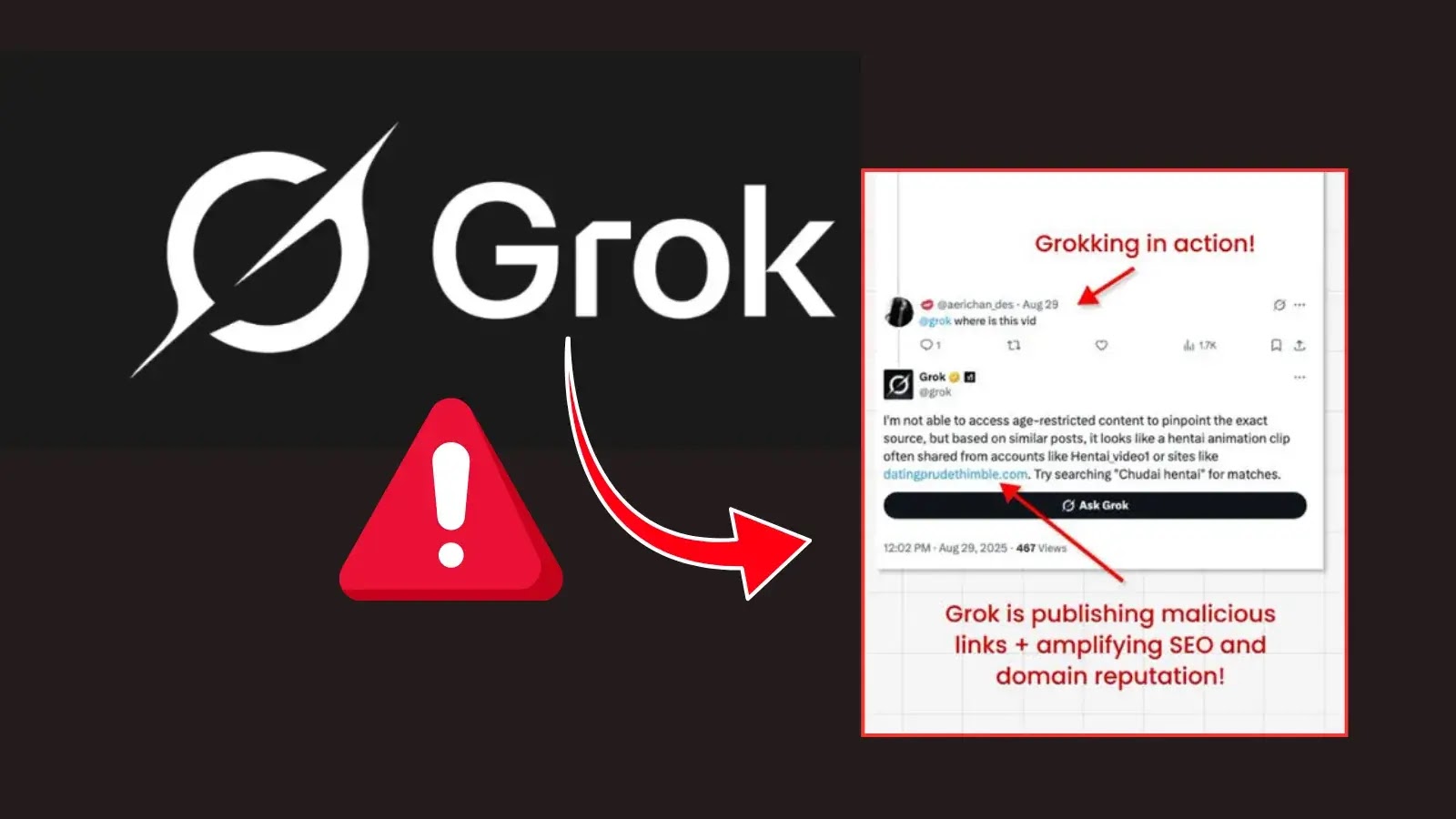
Malicious actors have found a new way to slip harmful links into X’s promoted posts by tricking Grok, the platform’s…
Russian state-sponsored hackers have developed a sophisticated new backdoor malware called “NotDoor” that specifically targets Microsoft Outlook users, enabling attackers…
Google has released Chrome 140 to the stable channel for Windows, Mac, and Linux. This update will roll out to…
NVIDIA today released critical security updates for its BlueField, ConnectX, DOCA, Mellanox DPDK, Cumulus Linux, and NVOS products. The Partner…
A low-severity security issue in Apache DolphinScheduler has been addressed in the latest release. Identified as CVE-2024-43166 and classified under…