Category: GBHackers
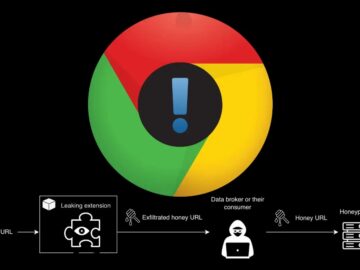
A new security investigation has uncovered 287 Chrome extensions that appear to secretly send users’ browsing data to remote servers, impacting an…
Operational Relay Box (ORB) networks are covert, mesh-based infrastructures used by advanced threat actors to hide the true origin of…
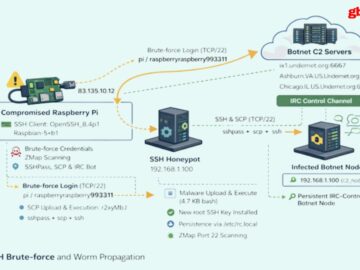
A DShield honeypot sensor recently recorded a complete compromise sequence involving a self-replicating SSH worm that exploits weak passwords to…
Feiniu fnOS network-attached storage (NAS) devices have been pulled into a large Netdragon botnet after attackers exploited still-unpatched vulnerabilities, turning…
The cybercrime group Muddled Libra (aka Scattered Spider, UNC3944). The contents of this rogue VM and activity from the attack…
Lazarus Group’s latest software supply chain operation is using fake recruiter lures and popular open‑source ecosystems to deliver malware to…
A critical vulnerability in the popular WPvivid Backup & Migration plugin is putting more than 800,000 WordPress websites at risk…
Google has released Chrome 145 to the stable channel for Windows, Mac, and Linux systems, addressing 11 security vulnerabilities that…
Palo Alto Networks has disclosed a PAN-OS firewall vulnerability that can let remote attackers force repeated reboots, potentially pushing a…
A newly discovered malicious NPM package, dubbed duer-js , is being used to distribute an advanced information‑stealing malware that primarily targets Windows…
A new fingerprinting technique called “Adbleed” reveals that VPN users aren’t as anonymous as they think. While VPNs hide your…
A dormant Microsoft Outlook add-in has been weaponized by attackers to steal thousands of login credentials and credit card numbers….