Category: GBHackers
The notorious Lazarus advanced persistent threat (APT) organization, which Qi’anxin internally tracks as APT-Q-1, has been seen using the ClickFix…
Cybersecurity experts discovered an advanced persistent threat (APT) cluster called ShadowSilk in a thorough research published by Group-IB. Since at…
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) has imposed sanctions on Russian national Vitaliy Sergeyevich…
Experts have described methods for mimicking the strategies of the advanced persistent threat (APT) group Scattered Spider in a recent…
Cisco has issued a high-severity security advisory warning of a dangerous vulnerability in its Nexus 3000 and 9000 Series switches…
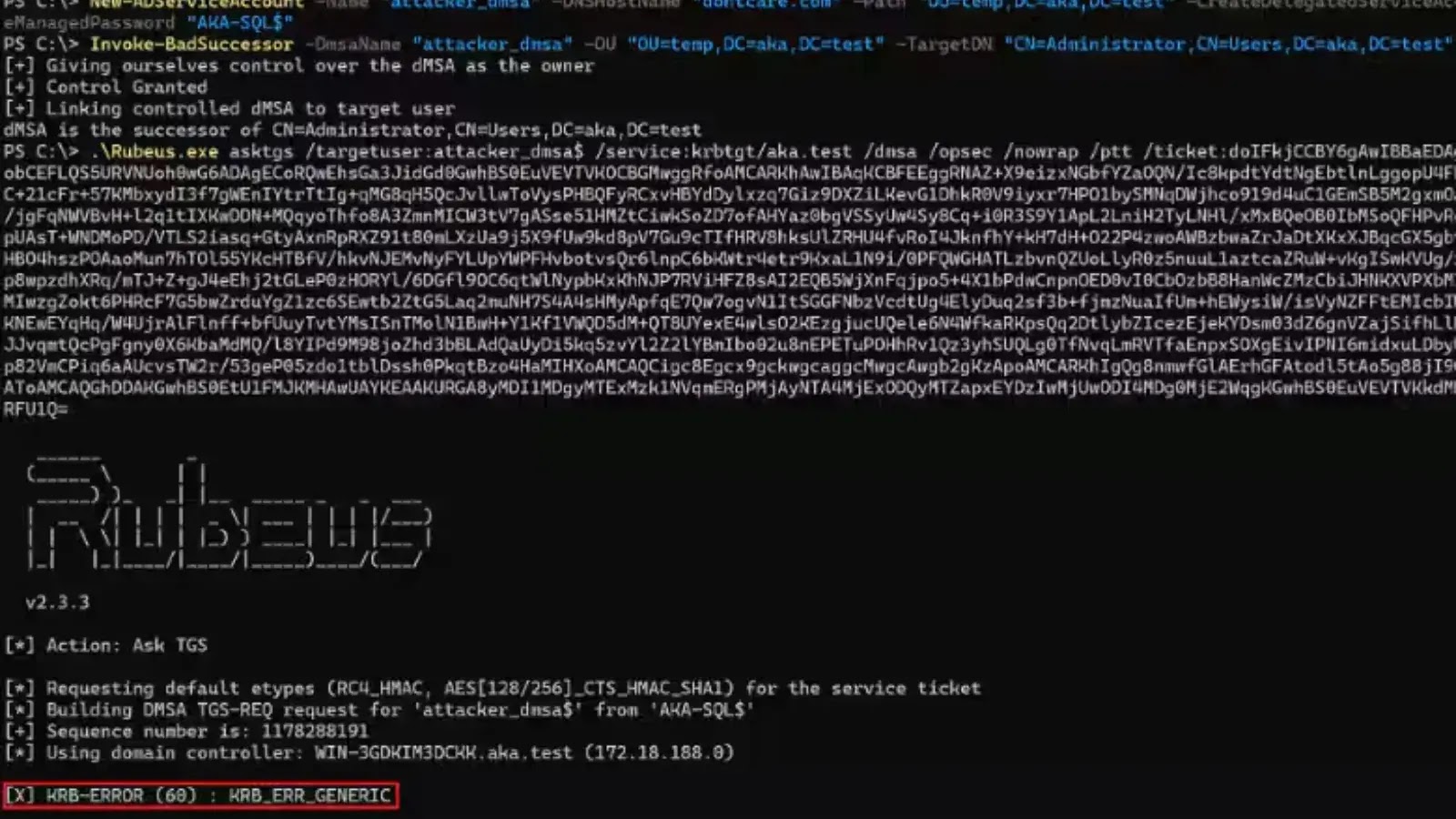
Akamai researchers evaluated Microsoft’s patch for the BadSuccessor vulnerability (CVE-2025-53779) to determine its scope and limitations. While the update effectively…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert after detecting active exploitation of a critical zero-day…
Cybersecurity researchers at Truesec have uncovered a sophisticated malware campaign distributing a weaponized PDF editor under the guise of “AppSuite…
A recent investigation has uncovered that relying solely on large language models (LLMs) to generate application code can introduce critical…
The Cybersecurity and Infrastructure Security Agency (CISA) unveiled a comprehensive Cybersecurity Advisory (CSA) designed to empower network defenders to detect,…
A critical zero-day remote code execution (RCE) vulnerability is currently threatening the security of over 28,000 Citrix instances worldwide. The flaw, designated…
A widespread service disruption is currently affecting Microsoft Teams users across the globe, preventing access to embedded Office documents within the collaboration…