Category: GBHackers
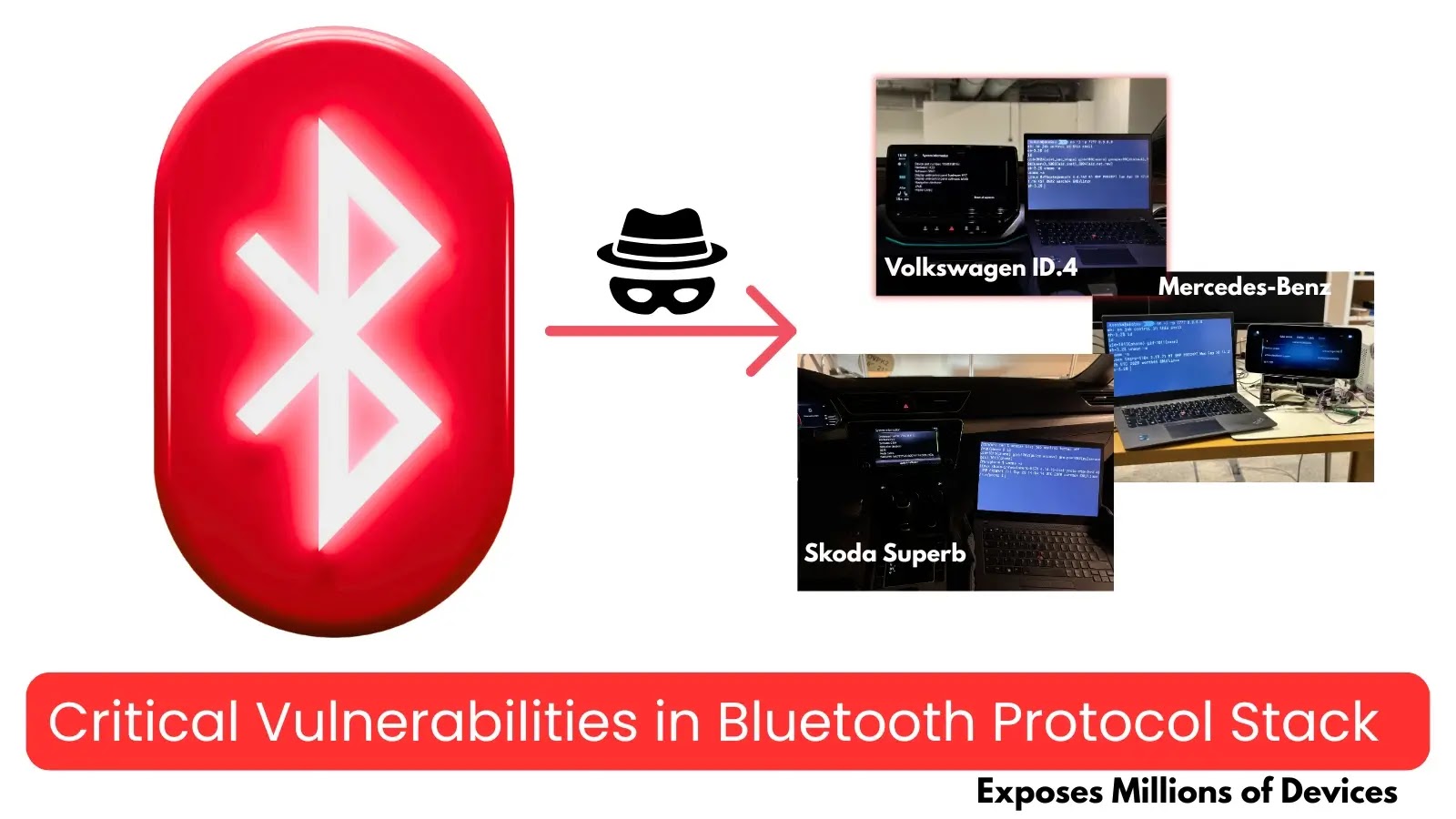
Security researchers have disclosed a critical set of Bluetooth vulnerabilities dubbed “PerfektBlue” that affect millions of vehicles and other devices…
Cary, North Carolina, July 10th, 2025, CyberNewsWire Industry’s Most Comprehensive Mobile Application Penetration Testing Program Addresses Real-World Mobile Security Challenges….
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical security advisory warning that multiple vulnerabilities in Emerson ValveLink…
UK law enforcement authorities have made significant progress in their investigation into cyber attacks targeting some of Britain’s most prominent…
Security researchers have identified a critical vulnerability in ServiceNow’s widely-used enterprise platform that could enable attackers to extract sensitive data…
Brave has taken a significant step toward empowering privacy-conscious Android users by making its browser fully available through its own…
Now, many global cryptocurrency investors view Bitcoin as a financial product for long-term investment rather than a simple speculative product….
Multiple critical vulnerabilities discovered in Ruckus Wireless management products pose severe security risks to enterprise networks, with issues ranging from…
The AhnLab Security Intelligence Center (ASEC) has confirmed that unpatched GeoServer instances are still facing relentless attacks by threat actors…
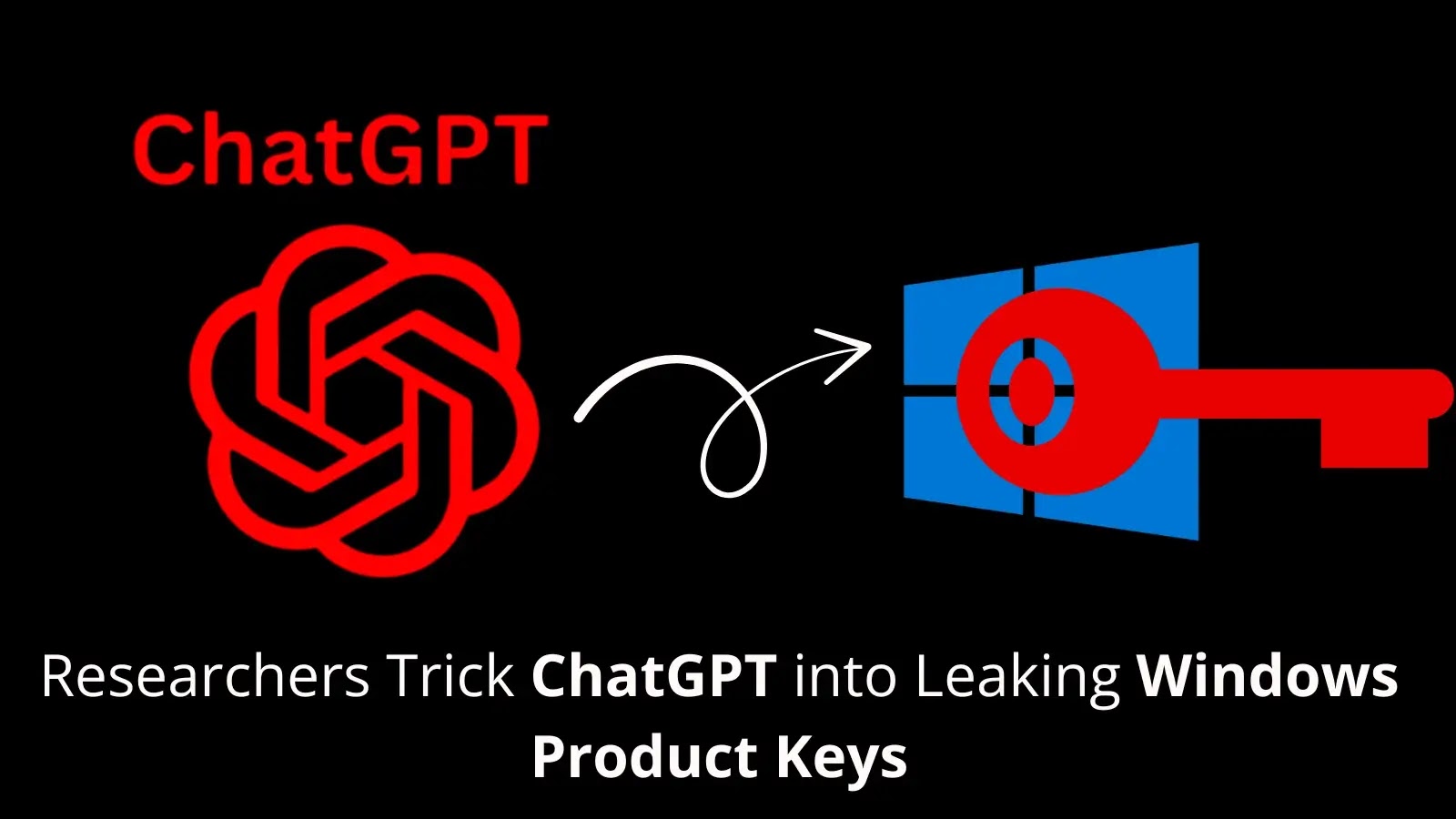
Security researchers have successfully demonstrated a sophisticated method to bypass ChatGPT’s protective guardrails, tricking the AI into revealing legitimate Windows…
The Qilin group emerged as the leading player in the ransomware ecosystem, which saw a notable rise in activity during…
A newly discovered man-in-the-middle exploit dubbed “Opossum” has demonstrated the unsettling ability to compromise secure communications over Transport Layer Security…