Category: GBHackers
Recent revelations about Google’s SafetyCore app have ignited a firestorm of privacy debates, echoing Apple’s recent controversy over photo scanning….
Security researchers have uncovered a novel Bluetooth tracking vulnerability in Apple’s Find My network – the system powering AirTags and…
Cybersecurity firm Group-IB, alongside the Royal Thai Police and Singapore Police Force, announced the arrest of a prolific hacker linked…
Cisco Systems has issued a critical security advisory for a newly disclosed command injection vulnerability affecting its Nexus 3000 and…
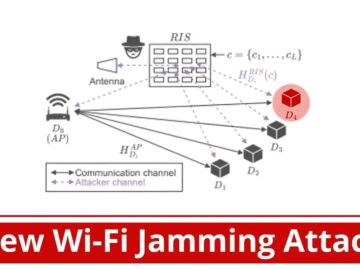
A newly discovered Wi-Fi jamming technique enables attackers to selectively disconnect individual devices from networks with surgical precision, raising alarms…
GitLab has urgently released security updates to address multiple high-severity vulnerabilities in its platform that could allow attackers to bypass…
A high-severity security vulnerability (CVE-2025-0514) in LibreOffice, the widely used open-source office suite, has been patched after researchers discovered it…
Cisco Systems has disclosed a high-severity vulnerability (CVE-2025-20111) in its Nexus 3000 and 9000 Series Switches operating in standalone NX-OS…
In a groundbreaking development, researchers have uncovered how attackers are exploiting Windows Virtualization-Based Security (VBS) enclaves to create malware that…
A recent discovery by cybersecurity researchers has revealed that the Poseidon malware, a macOS-targeting trojan, is leveraging PKG files with…
A financial management app named Finance Simplified has been revealed as a malicious tool for stealing sensitive user data and…
Recent cybersecurity investigations have uncovered a sophisticated technique employed by threat actors to evade detection during malware distribution. Attackers are…