Category: GBHackers
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) escalated its cybersecurity alerts on February 18, 2025, releasing two critical Industrial…
Google has rolled out an urgent security update for its Chrome browser, patching three vulnerabilities—including two critical heap buffer overflow…
A sophisticated cyber espionage campaign leveraging the EagerBee malware has been targeting government agencies and Internet Service Providers (ISPs) across…
The rise of customized large language models (LLMs) has revolutionized artificial intelligence applications, enabling businesses and individuals to leverage advanced…
Cybersecurity researchers have uncovered a new MageCart malware campaign targeting e-commerce websites running on the Magento platform. This attack exploits…
A significant vulnerability has been identified in large language models (LLMs) such as ChatGPT, raising concerns over their susceptibility to…
A recent study by researchers from the National University of Singapore and NCS Cyber Special Ops R&D explores how the…
A sophisticated malware campaign was launched by cybercriminals, targeting users through trojanized versions of popular games. Exploiting the holiday season’s…
SectopRAT, also known as Arechclient2, is a sophisticated Remote Access Trojan (RAT) developed using the .NET framework. This malware is…
A sophisticated malware campaign leveraging the Lumma InfoStealer has been identified, targeting educational institutions to distribute malicious files disguised as…
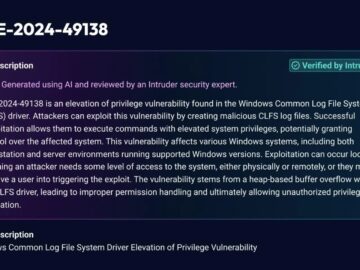
Intel by Intruder now uses AI to contextualize NVD descriptions, helping security teams assess risk faster. Intruder, a leader in…
Researchers from Trend Micro’s Threat Hunting team have uncovered a sophisticated cyberattack campaign by the advanced persistent threat (APT) group…