Category: GBHackers
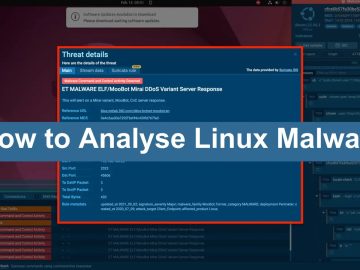
Linux, traditionally viewed as a more secure operating system than Windows, has experienced a notable increase in malware attacks. In…
In a startling revelation that has sent shockwaves through the cybersecurity community, a massive data leak has exposed the inner…
In a significant move against cybercrime, the U.S. government has announced a bounty of up to $15 million for information…
An updated version of the ObserverStealer known as AsukaStealer was observed to be advertised as malware-as-a-service that was capable of collecting…
Threat actors abuse Google Drive for several malicious activities due to its widespread use, easy file sharing, and collaboration features….
In a startling incident underscoring the growing menace of cybercrime, a woman’s Swiggy account was hacked, leading to fraudulent orders…
A new cybersecurity threat targeting Facebook advertisers in Vietnam, known as VietCredCare, has emerged. This information stealer has been active…
The malware, termed Migo by the creators, attempts to infiltrate Redis servers to mine cryptocurrency on the Linux host. The campaign employed…
Researchers have discovered that threat actors have been using open-source platforms and codes for several purposes, such as hosting C2…
Google has recently unveiled Chrome 122, a significant milestone for the widely used web browser. The most recent release, compatible…
Security Onion Solutions has recently rolled out the latest version of its network security monitoring tool, Security Onion 2.4.50. This…
VMware has issued an urgent advisory to administrators to remove a deprecated authentication plugin vulnerable to severe security threats. The…