Category: GBHackers
Security researchers have uncovered a severe unauthenticated Remote Code Execution vulnerability in Ubiquiti’s UniFi OS that earned a substantial $25,000…
The Open VSX team and Eclipse Foundation have addressed a significant security incident involving leaked authentication tokens and malicious extensions…
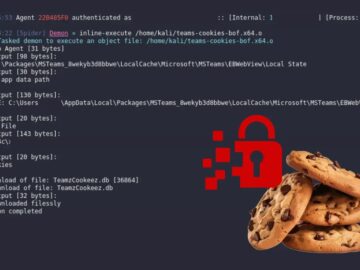
Cybersecurity researchers at Tier Zero Security have released a specialised Beacon Object File (BOF) tool that exploits a critical weakness…
Microsoft has acknowledged a persistent bug affecting Windows 11 versions 24H2 and 25H2 that prevents Task Manager from properly terminating…
A Ukrainian national accused of participating in one of the most damaging ransomware campaigns in history has been extradited from…
Privacy-focused technology company Proton has issued a warning about the escalating data breach crisis, revealing that hundreds of millions of…
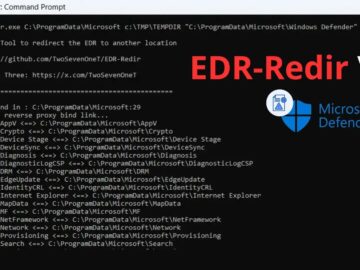
Security researcher TwoSevenOneT has released EDR-Redir V2, an upgraded evasion tool that exploits Windows bind link technology to bypass endpoint…
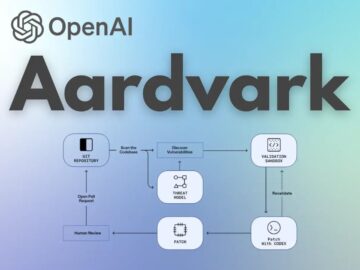
OpenAI has announced the launch of Aardvark, an autonomous AI security agent powered by GPT-5 that aims to revolutionize how…
Loss of internet access in rural areas is considerably more serious, as it disrupts education, work, and communication. Despite such…
The discovery of a large-scale NPM ecosystem compromise in September 2025 has renewed focus on email security as the critical…
The notorious Akira ransomware gang announced on October 29, 2025, that it successfully penetrated the systems of Apache OpenOffice, claiming…
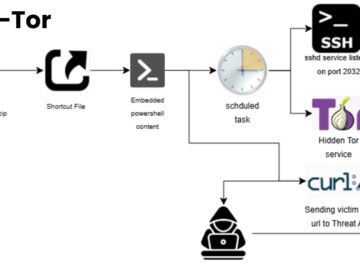
In October 2025, cybersecurity researchers at Cyble Research and Intelligence Labs (CRIL) uncovered a sophisticated malware campaign distributing weaponized ZIP…