Category: HackerCombat
In 2024, the cybersecurity landscape was shaken by an unexpected and widespread incident—the Snowflake data breach. Despite being a leading…
Cyber threats can wreak havoc on businesses, from data breaches to loss of reputation. Luckily, there are effective strategies available…
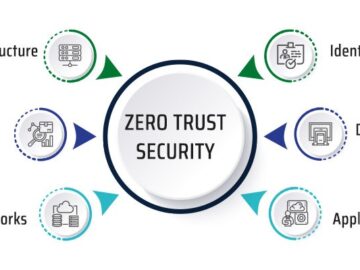
Zero trust security takes an “never trust, always verify” approach to access control. Access is only granted once an individual’s…
A Security Operations Center (SOC) specializes in monitoring and analyzing data to detect cyber threats and prevent attacks from them….
The Extended Detection and Response Platform (XDR) ingestion and correlation technology captures and correlates high-fidelity data across your security layers,…
Endpoint detection and response (EDR) tools offer businesses that employ hybrid work models or remote employees an extra layer of…
EDR can detect and respond to emerging and advanced cyber threats quickly and efficiently, making it an essential component of…
Cloud security involves employing perimeter defenses like firewalls, IDPSs and VPNs as well as guaranteeing isolation through network segmentation and…
Zero trust is an adaptable security framework designed to address today’s cyber security challenges. It employs microsegmentation and data-centric policies,…
Antivirus software protects devices against viruses, malware, and other cyberthreats by detecting, quarantining, and deleting malicious code. Modern antivirus products…
Computer viruses are extremely hazardous, which is why it’s crucial to secure your devices with reliable malware removal programs. These…
This attack had all the hallmarks of ransomware attack and targeted CDK Global systems used by auto dealerships to manage…