Category: HackRead
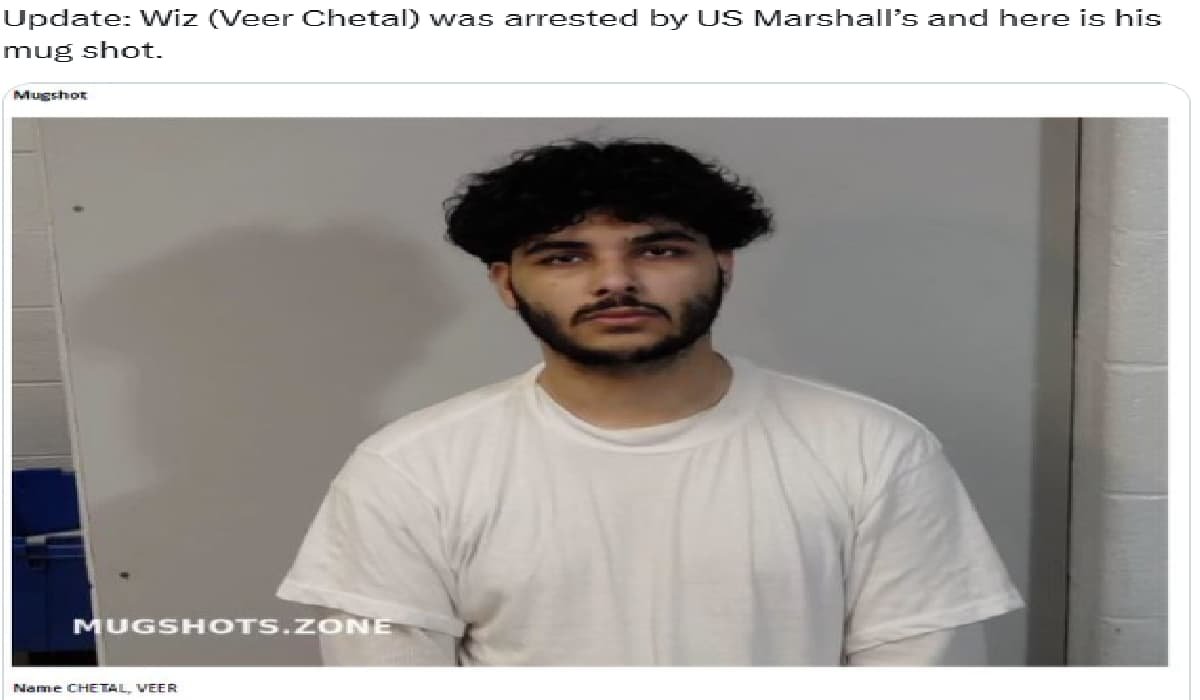
In a new development in the investigation of a massive $243 million cryptocurrency heist, one of the key suspects, Veer…
A recent collaborative effort by researchers Rachid Allam and Yasser Allam has exposed a critical vulnerability within the Next.js framework,…
Security researchers at ReversingLabs have discovered a new malware campaign on the npm package repository, revealing a new approach to…
Cary, North Carolina, March 27th, 2025, CyberNewsWire INE, a global leader in networking and cybersecurity training and certifications, is proud…
Cybersecurity threats are evolving at an unprecedented pace, leaving organizations vulnerable to large-scale attacks. Security breaches and data leaks can…
A recent discovery by cybersecurity researcher Jeremiah Fowler has shed light on a sensitive data exposure involving the Australian fintech…
The Internet Archive (Archive.org), home to the Wayback Machine, is temporarily offline due to a reported power outage. Engineers are…
A cybercriminal collective, known as Cloak, has confirmed its involvement in an attack targeting the Virginia attorney general’s office in…
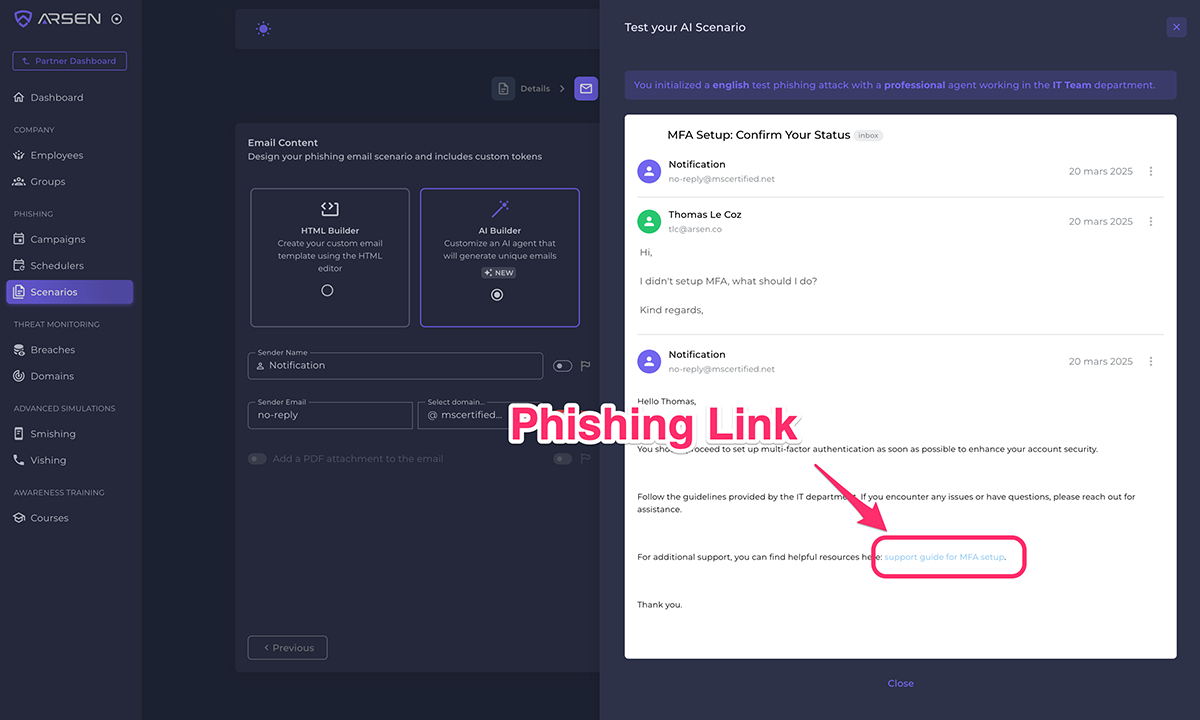
Paris, France, March 24th, 2025, CyberNewsWire Arsen, a leading cybersecurity company specializing in social engineering defense, today announced the full…
Gartner describes infrastructure as code (IaC) as a key way to unlock the potential of the cloud. However, some companies…
Cybercriminals are always looking for new ways to take advantage of people. One effective method they use is exploiting notification…
Counterfeit products are a growing problem in today’s market. With advancements in technology, counterfeiters have become more skilled at creating…