Category: HackRead
AI systems are becoming a huge part of our lives, but they are not perfect. Red teaming helps find weaknesses…
Cybercriminals are skilled at using public information to their advantage. Knowing how they gather this data can help you protect…
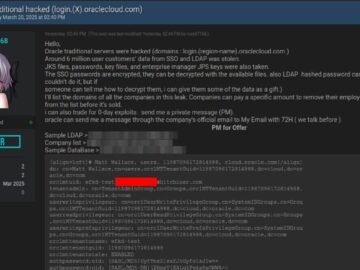
A recent investigation by CloudSEK’s XVigil platform has uncovered a cyberattack targeting Oracle Cloud, resulting in the exfiltration of six…
A new phishing campaign has been tricking users into giving out access to their Meta Business accounts especially Instagram. The…
Credential theft alert! Venak Security discovers a BYOVD attack using .SYS drivers to bypass Windows security. Learn how this attack…
ServiceNow vulnerability alert: Hackers are actively exploiting year-old flaws (CVE-2024-4879, CVE-2024-5217, CVE-2024-5178) for database access. Learn how to protect your…
Today, we are discussing Computer Vision applications, one of the most impactful AI-powered technologies that is reshaping our world, with…
Cybersecurity researchers at the Citizen Lab at the University of Toronto have exposed the use of sophisticated spyware named Graphite,…
Despite tighter security from Apple and Google, hackers and cybercriminals continue to exploit rooted and jailbroken devices for their attacks….
A new Windows zero-day vulnerability is being actively exploited by at least 11 hacking groups linked to nation-states including North…
Bengaluru, India, March 19th, 2025, CyberNewsWire Moving Beyond Detection to Real-Time, Automated Security Across Workloads, Cloud, and Infrastructure SecPod, a…
Cato Networks, a Secure Access Service Edge (SASE) solution provider, has released its 2025 Cato CTRL Threat Report, revealing an…