Category: HackRead
London, United Kingdom, March 5th, 2025, CyberNewsWire AI Soft has announced the upcoming public release of Alli AI, an advanced…
Veriti Research reveals 40% of networks allow ‘any/any’ cloud access, exposing critical vulnerabilities. Learn how malware like XWorm and Sliver…
Cofense uncovers new LinkedIn phishing scam delivering ConnectWise RAT. Learn how attackers bypass security with fake InMail emails and how…
Scammers are impersonating BianLian ransomware, and mailing fake ransom letters to businesses. Learn the red flags and how to protect…
Unit 42 uncovers JavaGhost’s evolving AWS attacks. Learn how this threat actor uses phishing, IAM abuse, and advanced evasion techniques,…
Boston and Tel Aviv, United States, March 4th, 2025, CyberNewsWire Pathfinder AI expands Hunters’ vision for AI-driven SOCs, introducing Agentic…
A new malware threat called Zhong Stealer has surfaced from China, and it’s already slipping into businesses through an unexpected…
Over 70% of marketers and small business owners in the world today use AI for SEO. That’s a staggering amount….
San Francisco, California, March 3rd, 2025, CyberNewsWire With the growing importance of security compliance for startups, more companies are seeking…
Security questionnaires take a lot of time and repetitively answering the same questions manually chews up business time but automation…
A new cyberattack campaign discovered by FortiGuard Labs, Fortinet’s threat intelligence and research unit, leverages a combination of social engineering,…
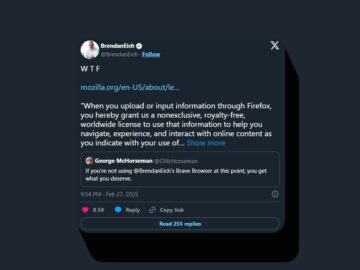
Firefox’s new Terms of Use spark user backlash over data rights. Learn how Mozilla responded to concerns about broad language…