Category: HackRead
Not getting enough views or traffic to your podcasts? Try this stunning AI audio-to-video generator to transform your podcasts into…
QR codes have become an everyday convenience, allowing quick access to websites, payment platforms, and digital menus with a simple…
Microsoft exposes Storm-2139, a cybercrime network exploiting Azure AI via LLMjacking. Learn how stolen API keys enabled harmful content generation…
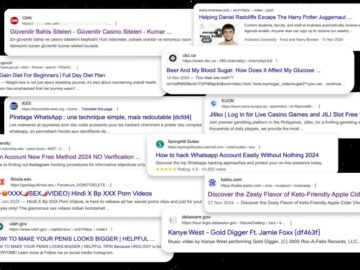
360XSS campaign exploits Krpano XSS to hijack search results & distribute spam ads on 350+ sites, including government, universities, and…
Louis Donald Mendonsa, 62, was sentenced following a guilty plea for distributing child sexual abuse materials (CSAM) via Dark Web…
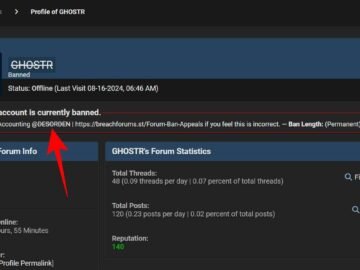
A coordinated effort between law enforcement in Thailand, Singapore, and cybersecurity firm Group-IB has led to the arrest of a…
Do you want to have the best communication system at your workplace? Learn how to maximize the benefits of Slack…
Auto-color: New Linux backdoor malware targeting the US and Asia. Learn about its advanced evasion, persistence, and detection methods. A…
FortiGuard Labs discovers Winos 4.0 malware targeting Taiwan via phishing. Learn how this advanced threat steals data and how to…
Cybersecurity researchers at Kaspersky’s Securelist have found a cyber espionage group known as Angry Likho APT (also referred to as Sticky Werewolf by some…
A data breach at DISA Global Solutions, a firm providing background checks, and drugs and alcohol testing services, exposed the…
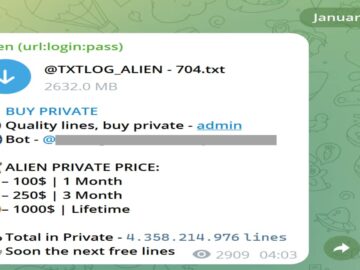
A massive collection of compromised data, dubbed “ALIEN TXTBASE,” has been integrated into the Have I Been Pwned, (a website…