Category: HackRead
Summary: Phishing Operation Dismantled: A joint effort by Belgian, Dutch authorities, and Europol dismantled a phishing gang that targeted victims…
Discover essential tips to secure your digital assets like crypto, NFTs, and tokens. Learn about wallet safety, avoiding phishing, 2FA,…
KEY POINTS Cybersecurity researchers at ReversingLabs found that hackers used malicious code to combine the Ultralytics AI library to mine…
Cryptocurrencies, from Bitcoin to altcoins and meme coins, revolutionize payments by offering privacy, reduced fees, faster transactions, enhanced security, and…
KEY POINTS of THIS STORY Operation Destabilise Success: The UK’s NCA led an international effort that dismantled two major Russian-speaking…
KEY POINTS DroidBot Discovery: A new Android spyware, DroidBot, was identified in mid-2024, operating as Malware-as-a-Service (MaaS). Targets and Tactics:…
SUMMARY Network Access: Chinese hackers maintained access to a major U.S. company’s network for at least four months, likely stealing…
eCommerce has become an essential part of our daily lives with hundreds of thousands of stores powered by Shopify, Magento,…
One Identity named Hot Company: Privileged Access Management (PAM) in 12th Cyber Defense Magazine’s Annual InfoSec Awards during CyberDefenseCon 2024. One Identity proudly…
Alisa Viejo, California, December 5th, 2024, CyberNewsWire One Identity named Hot Company: Privileged Access Management (PAM) in 12th Cyber Defense Magazine’s Annual…
SUMMARY Manson Market Takedown: Europol and international law enforcement dismantled the notorious Manson Market cybercrime platform, disrupting phishing networks and…
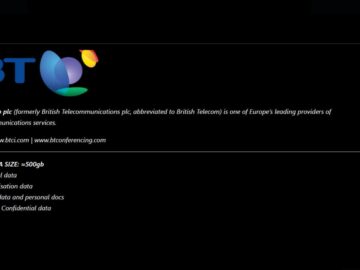
SUMMARY BT Group Ransomware Attack: British telecom giant BT Group’s Conferencing division was hit by a ransomware attack by Black…