Category: HackRead
Censys uncovers the hidden infrastructure of Fox Kitten, an Iranian cyberespionage group. It reveals unique patterns, potential new IOCs, and…
A server misconfiguration exposed a trove of documents belonging to FleetPanda, a leading petroleum and fuel industry software provider. Sensitive…
Austin, TX, September 18th, 2024, CyberNewsWire Research indicates that an infostealer malware infection is often a precursor to a ransomware…
Cary, North Carolina, September 18th, 2024, CyberNewsWire INE Security is proud to announce that it has been named a winner…
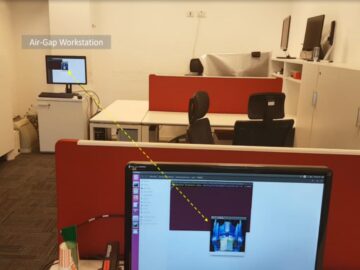
Discover the RAMBO attack, a groundbreaking method that uses electromagnetic waves to steal data from air-gapped systems. Learn how hackers…
RansomHub ransomware group leaks alleged 487 GB of sensitive data stolen from Kawasaki Motors Europe (KME), following a cyberattack. The…
Flare, the layer-1 blockchain for data, has introduced the Flare Time Series Oracle version 2 (FTSOv2) on its mainnet. This…
Boston, USA, September 16th, 2024, CyberNewsWire Analysis of millions of real-world NHI secrets by Entro Security Labs reveals widespread, significant…
A hacker known as IntelBroker claims to have breached the UK-based company Experience Engine, allegedly exposing sensitive data. The hacker…
A new Android malware called Trojan Ajina.Banker is targeting Central Asia – Discover how this malicious malware disguises itself as…
Singapore, Singapore, September 13th, 2024, CyberNewsWire SquareX has been named a winner of the prestigious Rising Star category in CybersecAsia…
A hacker claims to have stolen 440 GB of data from cybersecurity firm Fortinet, exploiting an Azure SharePoint vulnerability. The…