Category: HackRead
A recent National Crime Agency (NCA) investigation led to the arrest of a teenager in Walsall, England, linked to a…
Silver Spring, United States, September 12th, 2024, CyberNewsWire The investment will drive the company’s advancement of scalable workload access management…
Cybercriminals are increasingly targeting retail affiliate programs with sophisticated cryptocurrency scams. Retailers and customers must stay alert against domain fraud,…
Kransom ransomware hides within the StarRail game using DLL side-loading and a legitimate certificate from COGNOSPHERE PTE. LTD. Bypassing detection,…
Torrance, United States / California, September 11th, 2024, CyberNewsWire Criminal IP, a distinguished leader in Cyber Threat Intelligence (CTI) search…
DragonRank, a Chinese-speaking hacking group, has compromised 30+ Windows servers globally. They exploit IIS vulnerabilities to manipulate SEO rankings, distribute…
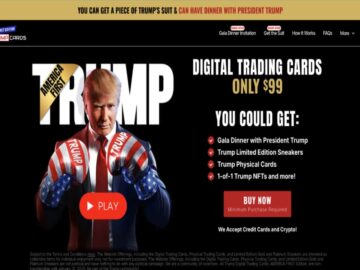
Cybercriminals target Trump’s digital trading cards using phishing sites, fake domains, and social engineering tactics to steal sensitive data. Scammers…
Small to medium-sized businesses (SMBs) are disproportionately targeted as cyber threats grow. According to the recent Hiscox annual cyber…
Palo Alto, USA/California, September 11th, 2024, CyberNewsWire Opus’ innovative engine integrates AI-driven intelligence, contextual data and automated decision-making to drive…
Microsoft September 2024 Patch Tuesday addresses 79 security vulnerabilities, including four actively exploited zero-days. It covers critical flaws in Windows…
Cary, North Carolina, September 10th, 2024, CyberNewsWire As cyber threats grow, small to medium-sized businesses (SMBs) are disproportionately targeted. According…
If you use the Internet, online privacy should be a growing concern as individuals share more personal information on various…