Category: HackRead
Fur Affinity’s domain and Twitter were compromised in a major DNS hijacking on August 20, 2024. Hackers redirected users to…
Cary, North Carolina, August 22nd, 2024, CyberNewsWire INE Security, a global cybersecurity training and certification provider, recently launched initiatives with…
Microchip Technology hit by cyberattack, disrupting manufacturing operations. A major disruption to semiconductor production has been reported, impacting the company’s…
Designers and engineers are always searching for tools to speed up their work and create more complex designs. Parametric modeling…
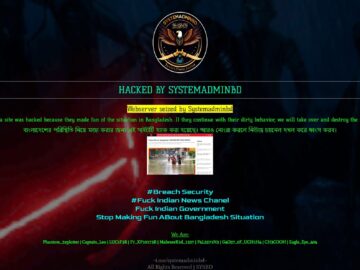
Bangladeshi hackers “SYSTEMADMINBD” defaced Zee Media’s website, accusing them of mocking the situation in Bangladesh amid severe flooding. The hack…
Millions of office and hotel contactless access cards using Fudan Microelectronics chips are vulnerable to a hardware backdoor allowing attackers…
The new PG_MEM malware targets PostgreSQL databases, exploiting weak passwords to deliver payloads and mine cryptocurrency. Researchers warn that 800,000…
ALBeast is a critical vulnerability that allows attackers to bypass authentication and authorization in AWS ALB-based applications. Learn how to…
Cybercriminals exploit Progressive Web Apps (PWAs) in the latest phishing scam, targeting mobile users in Czechia, Hungary, and Georgia. Learn…
Meet TodoSwift, a malicious application that masquerades as a PDF downloader. Crafted by the BlueNoroff threat group, TodoSwift leverages Apple’s Swift/SwiftUI…
Cary, North Carolina, August 20th, 2024, CyberNewsWire In modern business, cybersecurity is not merely a technical concern but a crucial…
Cisco Talos reveals 8 vulnerabilities in Microsoft’s macOS apps, exploiting TCC framework weaknesses. Hackers can bypass security, inject malware, and…