Category: HackRead
In summary: The report covers the first quarter of 2024 and shows that a North Korean hacker group called Kimsuky…
Top-notch stores are moving online as eCommerce continues to lead with breakthrough innovations that are transforming global business operations and…
Kaspersky researchers have identified multiple security vulnerabilities in Cinterion cellular modems, which could potentially be exploited by threat actors to…
Encrypted email providers like Proton Mail and Wire provide end-to-end encryption, ensuring only the sender and recipient can read the…
London, United Kingdom, May 13th, 2024, CyberNewsWire Logicalis, the global technology service provider delivering next-generation digital managed services, has today…
Torrance, California, May 13th, 2024, CyberNewsWire Criminal IP, a renowned Cyber Threat Intelligence (CTI) search engine developed by AI SPERA,…
Londoners were met with a rather unusual sight this week as part of a thought-provoking marketing campaign by virtual private…
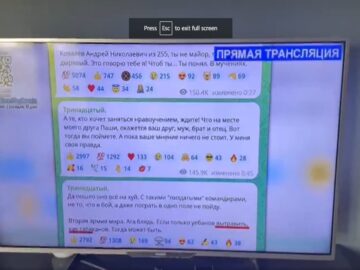
Imagine turning on your TV for the morning news and seeing a military parade of another country instead! That’s what…
The notorious hacker known as IntelBroker claims to have successfully breached the European Union Agency for Law Enforcement Cooperation, commonly…
The world of artificial intelligence (AI) is rapidly evolving, offering incredible potential for innovation and progress. However, with great power…
Dell Inc., the technology giant, has notified its customers of a data breach. According to an email obtained by Hackread.com,…
The infamous IntelBroker hacker claims to have breached a third-party contractor and stolen sensitive data belonging to two prominent banks…