Category: HackRead
Fortinet has classified both security vulnerabilities as critical. Additionally, CISA has updated its Known Exploited Vulnerabilities (KEV) Catalog with pertinent…
In the rapidly evolving world of digital commerce, cryptocurrencies have emerged as a game-changer, with Ethereum at the forefront. For…
The Trojan.MAC.RustDoor backdoor is potentially linked to the notorious BlackBasta and (ALPHV/BlackCat) ransomware operators. Bitdefender researchers have discovered a new…
Stay alert against Temu phishing scams: Cybersecurity experts warn of scammers using fake giveaways to steal credentials. Over 800 new…
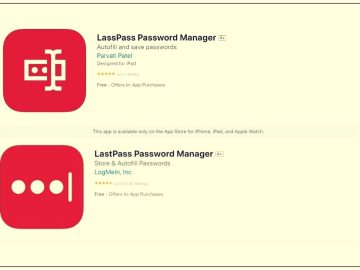
The popular LastPass Password Manager application has warned iOS users about a fraudulent app exploiting the app’s name circulating on…
Uncover the risks posed by a data leak exposing over 3 million vulnerable records, internal communications, client details, and plaintext…
In the fast-paced world of fintech, automation promises convenience and profitability. Trading bots, algorithms programmed to execute trades based on…
The Dutch intelligence services have warned about a growing trend of threat actors targeting edge devices, such as VPNs, email…
The data breaches, originating from SIM-swapping attacks, occurred in November 2023 and have since sparked widespread concerns about data security….
Delve into automated versus manual API testing for efficient software delivery. See how automation speeds validation while manual testing provides…
The Shadowserver Foundation reports that a zero-day vulnerability, CVE-2024-21893 (CVSS score 8.2), disclosed by Ivanti on 31 January 2024, is…
Since emerging in November 2023, ResumeLooters has exploited SQL injection and XSS vulnerabilities to compromise over 65 job-seeking websites. In…