Category: HackRead
Soap2day permanently shut down in June 2023 – While the official site and its major mirror sites closed down, it…
It is a well-known fact that cybercriminals have evolved over the years. The emergence of AI-powered malicious chatbots, such as…
Pwn2Own Automotive 2024 took place in Tokyo, Japan, from January 24 to 26. Pwn2Own Automotive 2024, a three-day contest organized…
The cybersecurity researchers at Kaspersky have uncovered more than 3,000 posts on the dark web, where threat actors seek to…
The Blackwood APT is using the NSPX30 backdoor in cyberespionage attacks against individuals and companies in China, Japan, and the…
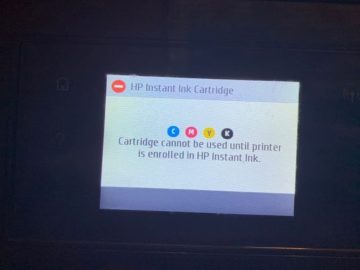
The company now claims that allowing third-party ink cartridges in its printers would expose them to viruses and malware. Hewlett-Packard…
Powerloom, the composable data network, has just announced a partnership with Polygon Network. In a first-of-its-kind event on Polygon, Powerloom…
Pwn2Own Automotive 2024 takes place in Tokyo, Japan, from January 24 to 26. The Pwn2Own Automotive 2024 hacking contest, taking…
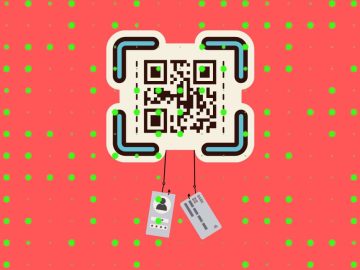
Check Point’s Live Cyber Threat Map identified 20,000 instances of QR code phishing and malware attacks within two weeks, highlighting…
As per the data breach notification filed by the company with Maine’s attorney general office, hackers gained access to customers’…
The report outlines that Artificial Intelligence (AI), currently utilized by cybercriminals, is lowering entry barriers for less experienced threat actors,…
The staggering 198.3 gigabytes of misconfigured database contained more than 260,000 records including customer selfies with unredacted credit cards. Cybersecurity…