Category: HackRead
All users are encouraged to upgrade to the latest version of Curl as soon as possible. Two security vulnerabilities have…
The largest DDoS attack on the Internet has occurred, following the exploitation of a new zero-day vulnerability by hackers. Google,…
Google is making passkeys the default option, aiming to replace passwords altogether. Google announced today that it is making passkeys…
Thousands of WordPress websites have been hacked as hackers exploit a vulnerability in the tagDiv Composer front-end page builder plugin….
A Magecart attack is a type of digital credit card skimming attack where malicious code is injected into e-commerce websites…
Here are simple yet vital steps to identify online trading scams and safeguard your investments from cyber criminals. In today’s…
Amidst the escalating conflict between Palestine and Israel, both pro-Palestinian and pro-Israeli hacktivists are targeting critical Industrial Control Systems (ICS)…
Penetration testing is vital as it helps identify vulnerabilities in a system or network, allowing organizations to proactively strengthen their…
AIM-listed British power and data transmission products manufacturer Volex PLC is the latest victim of a cyberattack. KEY FINDINGS A…
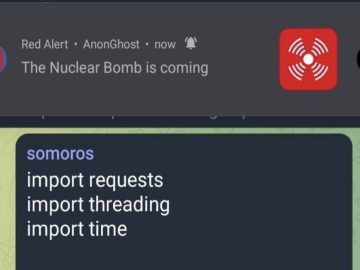
Pro-Palestinian hackers from AnonGhost apparently managed to hack the Red Alert app, whose sole purpose is to send missile and…
Check Point’s Global Threat Index for September 2023, released on October 6th, revealed that Education and Research remain the top…
A new report from the cybersecurity firm Human Security confirms the presence of two backdoors, Badbox and Peachpit, in popular…