Category: HackRead
RateForce is a platform that facilitates online comparison of car insurance quotes and has boasted nearly 11 million quotes since…
US military personnel have become unsuspecting recipients of unsolicited smartwatches delivered straight to their mailboxes. Recent reports indicate that these…
The vCISO Directory comes to answer the increasing need of SMBs to manage their cybersecurity and helps them find and…
The NOBELIUM hackers have been linked to Russia and are known for targeting the SolarWinds hack in 2021. Microsoft has…
Condi is the second DDoS botnet to exploit CVE-2023-1389, with the Mirai botnet targeting it in April 2023. FortiGuard Labs…
The Swing VPN app, which is available on the official Google Play Store under the name Swing VPN – Fast…
Allegedly, the satellite in question is purportedly owned by Maxar Technologies, a prominent US-based space technology firm, while it has…
This was discovered by Group-IB’s cybersecurity researchers, who noted that 100,000 devices were infected by Raccoon, Vidar, and Redline malware,…
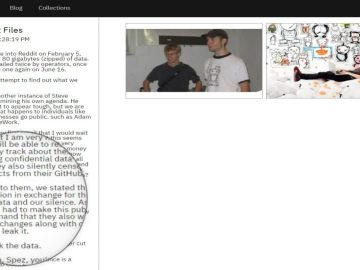
The ransomware gang has also issued a threat to leak the alleged stolen data unless Reddit complies with their demands….
Previously, threat actors took over misconfigured databases to demand ransom, but now there has been a change in their tactics….
Protect your online privacy with trustworthy VPNs. Shield your sensitive data from prying eyes and browse the internet safely from…
Are you looking to switch your web address to another registrar? According to ICANN, you’re free to do so outside…