Category: HackRead
CurseForge, a gaming platform that offers a wide range of video game modifications and add-ons, has released a tool to…
In May 2023, Christian Selig, the developer behind the Apollo app, revealed that Reddit was demanding $12,000 for a mere…
In addition to the rise in botnet-driven DDoS attacks, the Threat Intelligence Report highlights a doubling in the number of…
World Mobile, a decentralized wireless network operator, has achieved a significant milestone with the successful completion of field tests for…
The issue allows attackers to exploit ChatGPT’s tendency to generate false information, particularly in the form of nonexistent code packages….
The Stealth Soldier campaign marks the possible reappearance of a threat actor known as “The Eye on the Nile” since…
The innovative approach, known as “picture in picture,” capitalizes on users’ trust in familiar logos and promotions, making the attacks…
Have you ever tried to access a website only to find that it’s difficult or impossible to navigate? This is…
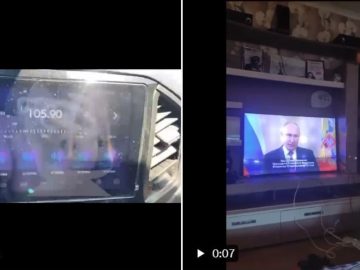
During the cyber attack, a hacker compromised radio and TV broadcasts and transmitted a fabricated message from President Vladimir Putin….
The malware-infected apps include a variety of industries, including gaming, anti-virus, VPN, tutorials, gaming, social media and many more. Bitdefender,…
These 2 billion SWEAT tokens, which make up around 13% of the total supply, have been locked in inactive user…
With over 500,000 downloads from the Google Play Store alone, i2VPN boasts a significant user base. In a recent cybersecurity…