Category: HackRead
The notorious Inc ransomware group has taken responsibility for an August 2025 data breach at the Pennsylvania Attorney General’s office….
Every SOC leader understands that faster threat detection is better. But the difference between knowing it and building a system…
Stellantis, the global automaker behind brands like Jeep, Chrysler, Dodge and FIAT, confirmed a data breach affecting its North American…
Not long ago, the mere idea that cryptocurrencies could ever be integrated into mainstream finance would have seemed like a…
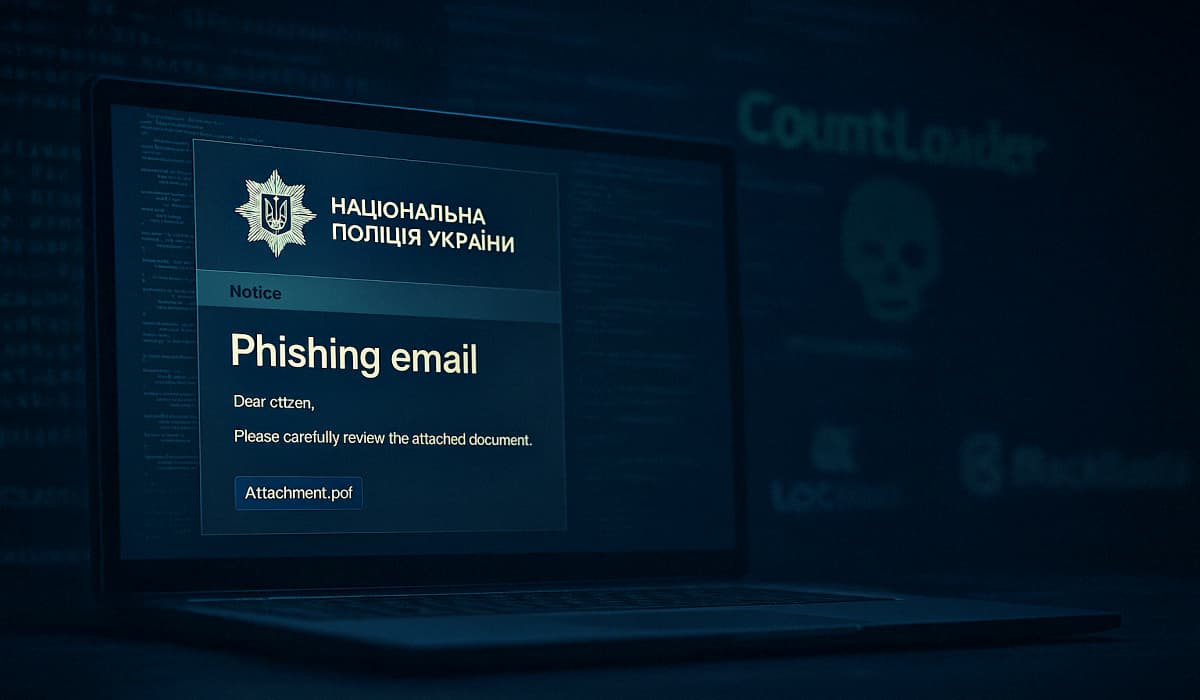
New research from cybersecurity firm Silent Push reveals that Russian ransomware gangs are using a new type of malicious program,…
An international police taskforce has identified 51 children in an operation targeting online child sexual exploitation, Europol confirmed today. The…
An international police taskforce has identified 51 children in an operation targeting online child sexual exploitation, Europol confirmed today. The…
A team of security researchers from Cloud Security Solutions provider, Radware, found a way to trick a popular AI tool…
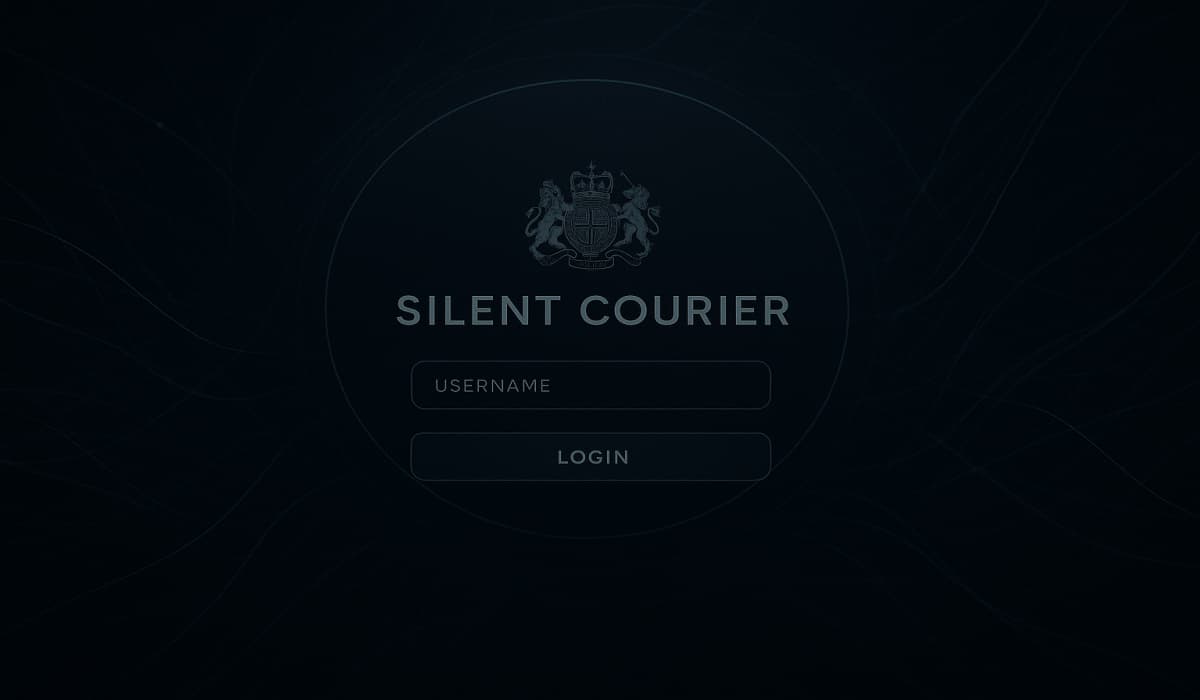
The UK’s foreign intelligence service, MI6, has launched a new platform for potential agents to get in touch. Announced on…
The UK’s foreign intelligence service, MI6, has launched a new platform for potential agents to get in touch. Announced on…
Travellers moving through some of Europe’s busiest airports faced long lines and delays on Friday after a cyberattack disrupted check-in…
A recent investigation by cybersecurity firm CloudSEK has exposed a major operation based in China that is selling high-quality, counterfeit…