Category: HackRead
LevelBlue Labs has published new research on a recent attack that used a fileless loader to deliver AsyncRAT, a well-known…
Sofia, Bulgaria, September 10th, 2025, CyberNewsWire Kikimora, a cybersecurity specialist and a product developer, has announced the launch of Kikimora…
An unsecured database managed by Hello Gym has exposed over 1.6 million audio recordings of gym members. Learn why this…
Cybersecurity researchers at Point Wild’s Lat61 Threat Intelligence Team have released new findings on a highly malware operation known as…
A new, sophisticated phishing kit, Salty2FA, is using advanced tactics to bypass MFA and mimic trusted brands. Read expert analysis…
Republic today announced a strategic partnership with Incentiv, an EVM-compatible Layer 1 blockchain designed to make Web3 simple, accessible, and…
Akamai’s Hunt Team has reported a new variant of malware targeting exposed Docker APIs, expanding on a campaign first documented…
Silver Spring, USA, September 9th, 2025, CyberNewsWire Fast Company today announced its seventh-annual Best Workplaces for Innovators list, recognizing businesses…
Aikido Security flagged the largest npm attack ever recorded, with 18 packages like chalk, debug, and ansi-styles hacked to hijack…
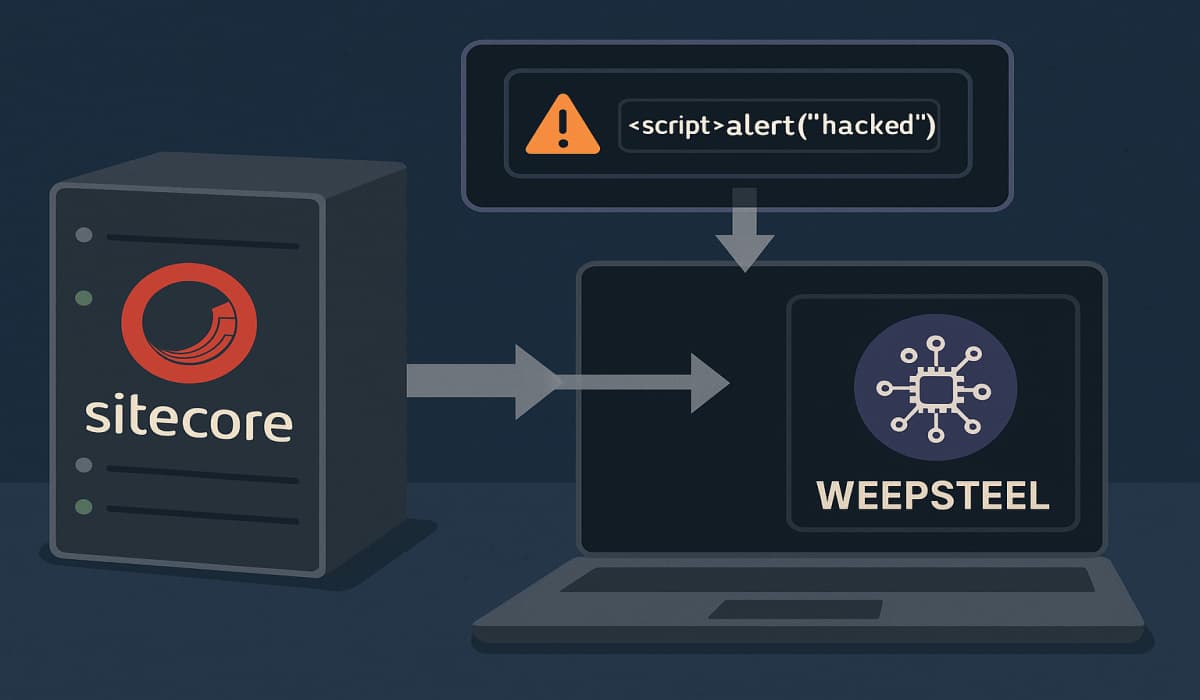
A critical zero-day vulnerability (CVE-2025-53690) is being actively exploited in Sitecore. This flaw, originating from old, insecure keys, allows hackers…
MostereRAT malware targets Windows through phishing, bypasses security with advanced tactics, and grants hackers full remote control. Cybersecurity researchers at…
Paris, France, 2025 – iExec has announced the deployment of its privacy framework on Arbitrum, enabling the creation of powerful…