Category: HackRead
AgentFlayer is a critical vulnerability in ChatGPT Connectors. Learn how this zero-click attack uses indirect prompt injection to secretly steal…
A Nigerian man has been extradited from France to face hacking, identity theft, and fraud charges in the US. He…
Critical WinRAR flaw CVE-2025-8088 exploited by Russia-linked hackers to spread RomCom malware, update to version 7.13 now to stay protected….
A new report by VulnCheck exposes a critical command injection flaw (CVE-2025-53652) in the Jenkins Git Parameter plugin. Find out…
A sophisticated and large-scale cybercrime campaign, named GreedyBear, has been exposed for stealing at least a million dollars from cryptocurrency…
In a recent revelation, Google has confirmed that one of its internal databases was breached by a well-known cybercriminal organization….
Cybersecurity researchers at SafeBreach Labs have uncovered a new kind of cyberattack that starts with something as ordinary as a…
Cybersecurity researchers at SafeBreach Labs have uncovered a new kind of cyberattack that starts with something as ordinary as a…
Menlo Park, California, USA, August 7th, 2025, CyberNewsWire AccuKnox, a global leader in Zero Trust Cloud Native Application Protection Platforms…
The luxury fashion brand Chanel has announced that it suffered a data breach, affecting some of its customers in the…
Menlo Park, California, USA, August 7th, 2025, CyberNewsWire AccuKnox, a global leader in Zero Trust Cloud Native Application Protection Platforms…
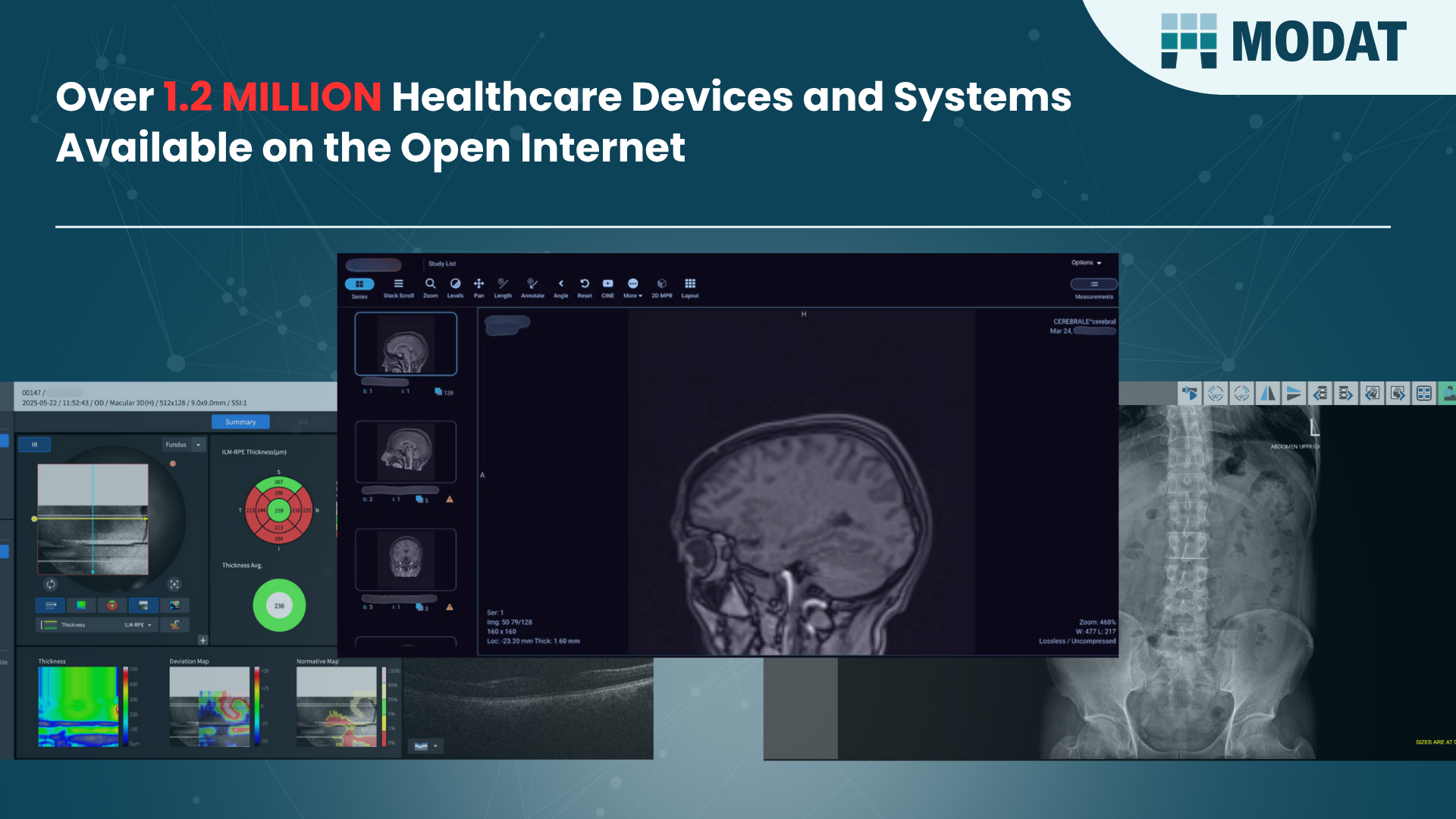
The Hague, Netherlands, August 7th, 2025, CyberNewsWire Over 1.2 million internet-connected healthcare devices and systems with exposure that endangers patient…