Category: HackRead
Telecom giant AT&T has agreed to a $177 million settlement to resolve two major lawsuits stemming from widespread data breaches…
The newly formed SatanLock ransomware group has announced it is shutting down. Before disappearing, however, the group says it will…
A series of malicious apps and stealthy spyware is targeting Android users worldwide, with new data showing how cybercriminals keep…
Cybersecurity threats have emerged so quickly that most companies struggle to keep up and executives are often the first targets….
Effective onboarding is essential in fast-paced hospitality, with high turnover rates and a multitude of expectations as the baseline for…
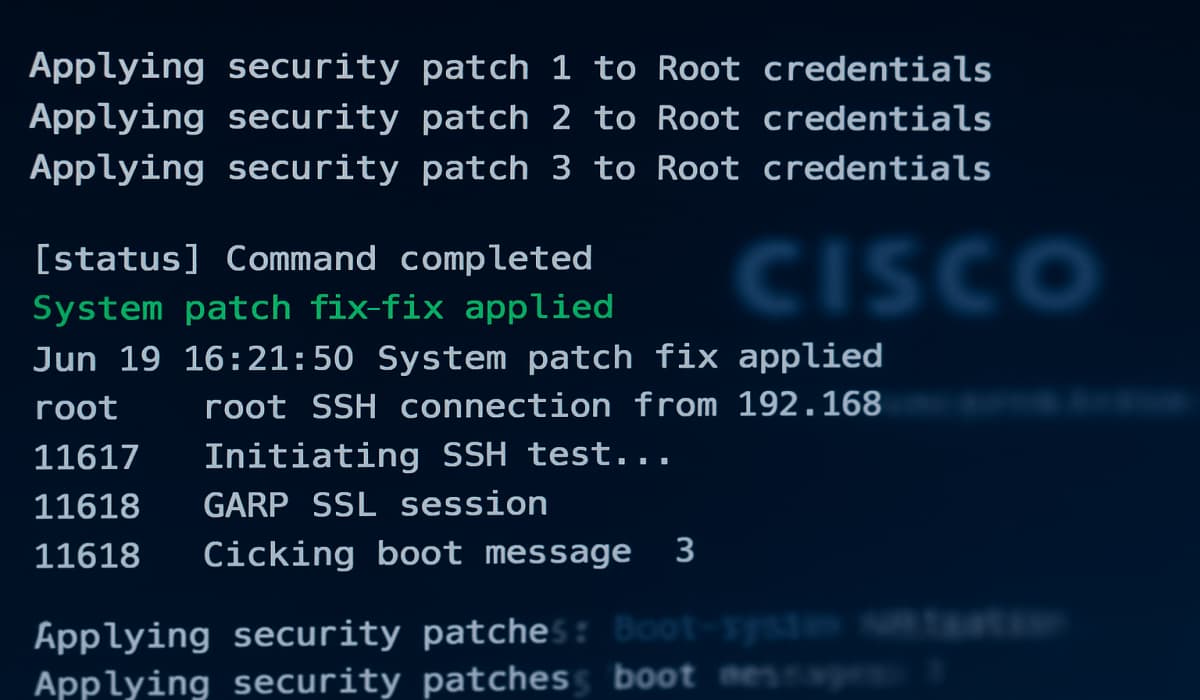
Cisco, a leading networking hardware company, has issued an urgent security alert and released updates to address a severe vulnerability…
Hunters International ransomware gang closes after 55 confirmed and 199 unconfirmed cyberattacks. Read about its rebrand to World Leaks and…
Email is still the backbone of how businesses communicate, with more than 300 billion messages sent every day. But this…
Cybersecurity firm Silent Push has exposed a massive phishing scam originating from China, which has created thousands of fake e-commerce…
A new report from SentinelLabs, released on July 2, 2025, reveals a sophisticated cyberattack campaign targeting Web3 and cryptocurrency companies….
In a report published by ANSSI on July 1, 2025, the French cybersecurity agency revealed a highly skilled cybercrime group,…
Once upon a time, say, 2016, Ethereum was a curious new arrival in the crypto space. It promised more than…