Category: HackRead
Cybersecurity experts at SecurityScorecard have discovered a widespread cyber espionage operation, dubbed LapDogs, which has compromised an unknown number of…
DUBAI, United Arab Emirates, June 23rd, 2025, CyberNewsWire Five dedicated bug bounty programs upgraded across 1inch core components, including smart…
Newark, United States, June 23rd, 2025, CyberNewsWire The OpenSSL Corporation and the OpenSSL Foundation are issuing a final call for…
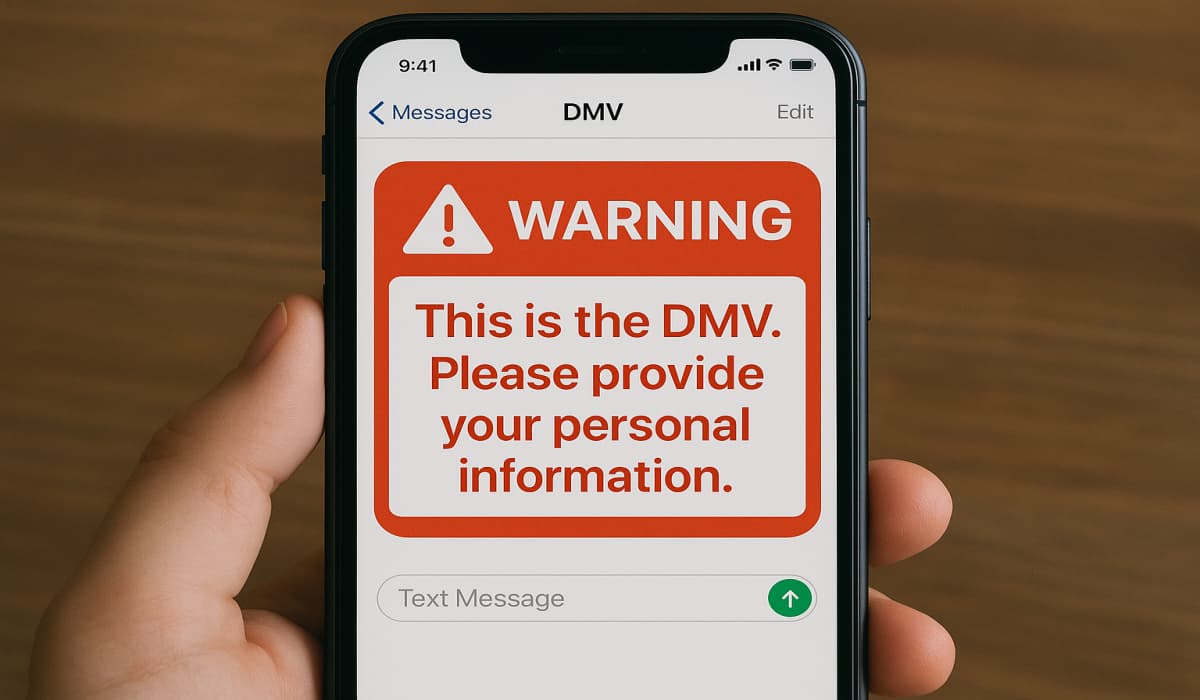
A series of fraudulent text messages impersonating state Departments of Motor Vehicles (DMVs) has spread throughout the United States tricking…
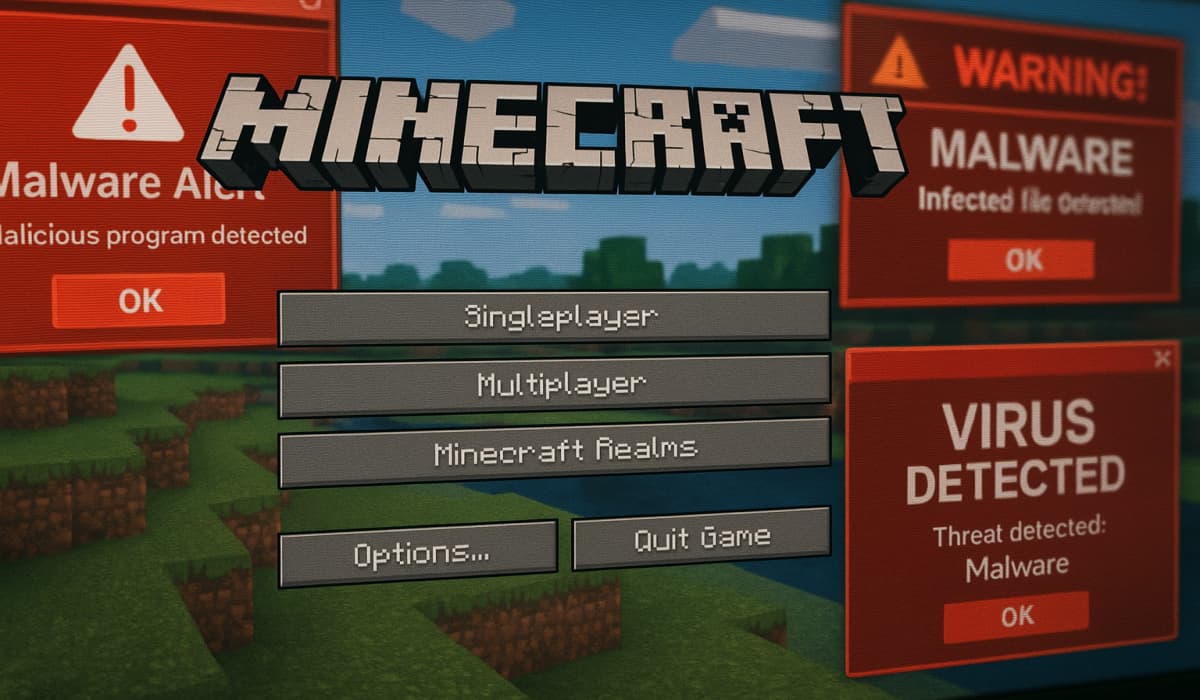
A new malware campaign has been targeting Minecraft players through fake mod downloads, according to recent findings from Check Point…
A serious security vulnerability, tracked as CVE-2023-28771, is affecting Zyxel networking devices. Security researchers at GreyNoise noticed a sudden sharp…
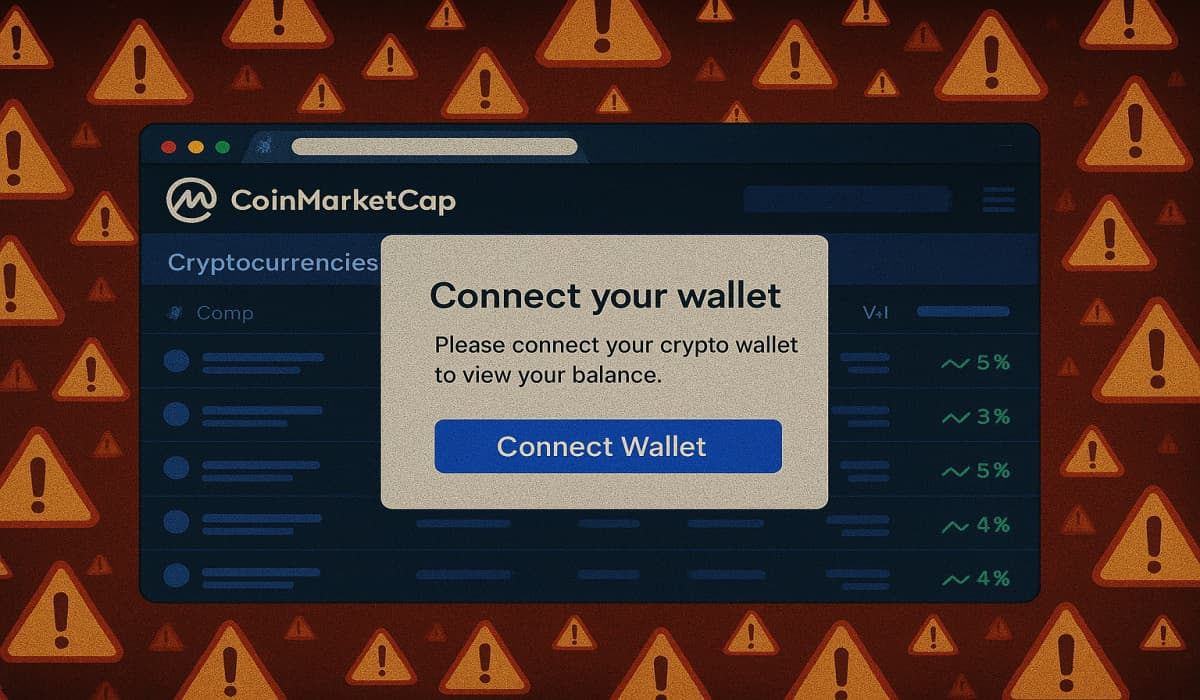
A coordinated crypto theft operation targeting CoinMarketCap users has been exposed after leaked images surfaced from a Telegram channel known…
A new joint report released today by FS-ISAC, a non-profit organization focused on financial cybersecurity, and Akamai Technologies, a leading…
European law enforcement agencies, led by Denmark and Sweden, are intensifying their fight against a disturbing new criminal trend: the…
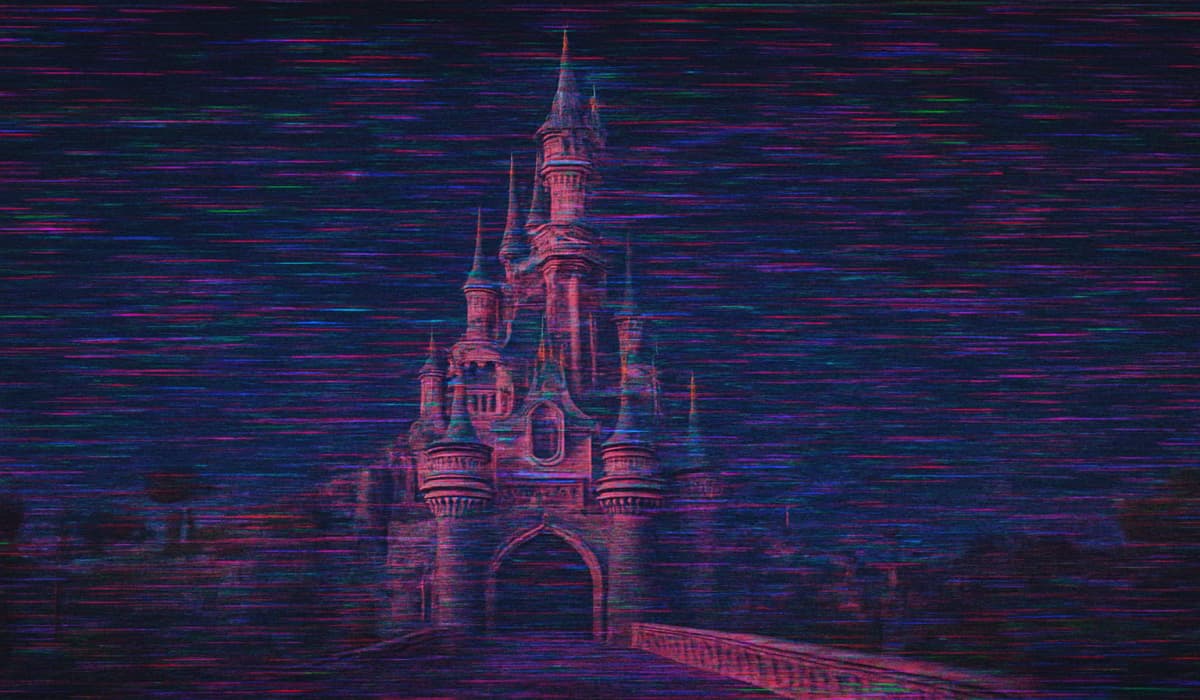
The infamous Anubis ransomware gang has listed Disneyland Paris as its latest victim. Hackread.com can confirm that the group posted…
Cybersecurity experts at Varonis Threat Labs have identified a clever new way to spot hidden cyberattacks, even those used by…
A new and highly sophisticated cyberattack, believed to be from a Russian state-linked group, has been revealed. This innovative method…