Category: HackRead
Accidentally deleted some photos from your iPhone? You’re definitely not alone; most iPhone users have done it at some point….
The Growing Threat of Digital Identity Theft Identity theft is a continuous online threat that lurks behind every login, transaction,…
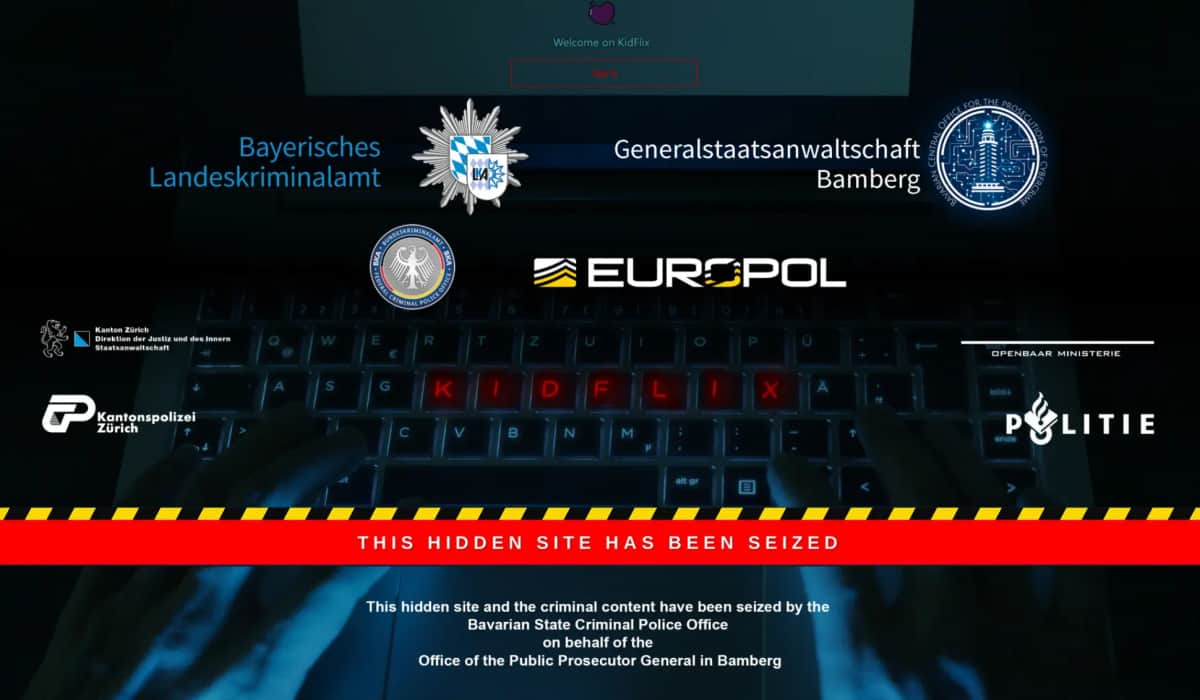
In a major international crackdown, law enforcement agencies have taken down “Kidflix,” one of the largest known child sexual abuse…
Royal Mail Group, the UK’s centuries-old postal institution, has allegedly suffered a massive data breach resulting in the leak of…
A recent investigation by ESET researchers has shed light on the continued activities and evolving toolset of the China-aligned Advanced…
The Microsoft Offensive Research and Security Engineering (MORSE) team has identified a crucial security vulnerability within a range of Canon…
Delaware, USA, April 2nd, 2025, CyberNewsWire Brinker, an innovative narrative intelligence platform dedicated to combating disinformation and influence campaigns, has…
In the competitive world where artificial intelligence (AI) has made it easy to use technology, companies are constantly looking for…
Data protection is of the highest importance in 2025. With growing numbers of organizations handling sensitive customer data and stricter…
The state of Texas is now at the center of a legal firestorm after a class action lawsuit was filed…
Ontinue’s Cyber Defense Centre (CDC) recently investigated an incident that shows how a simple vishing call can turn into a…
The cryptocurrency world feels like a wild ride full of risks, twists, and big dreams of building wealth. In its…