Category: HelpnetSecurity
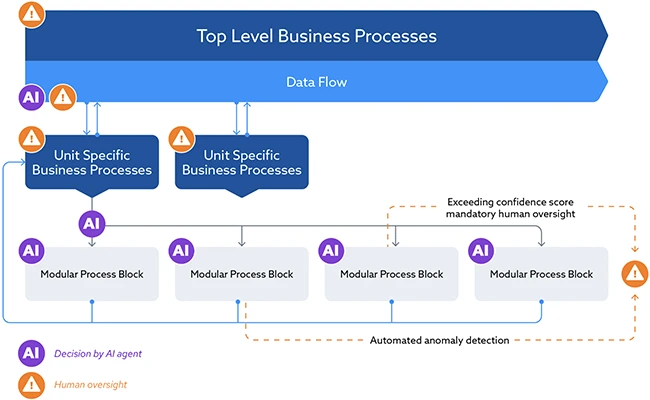
AI is supposed to make businesses faster, smarter, and more competitive, but most projects fall short. The Cloud Security Alliance…
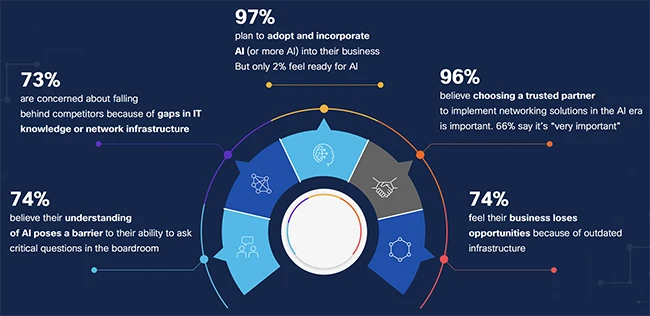
As AI assistants, agents, and data-driven workloads reshape how work gets done, they’re creating more latency-sensitive, and more complex network…
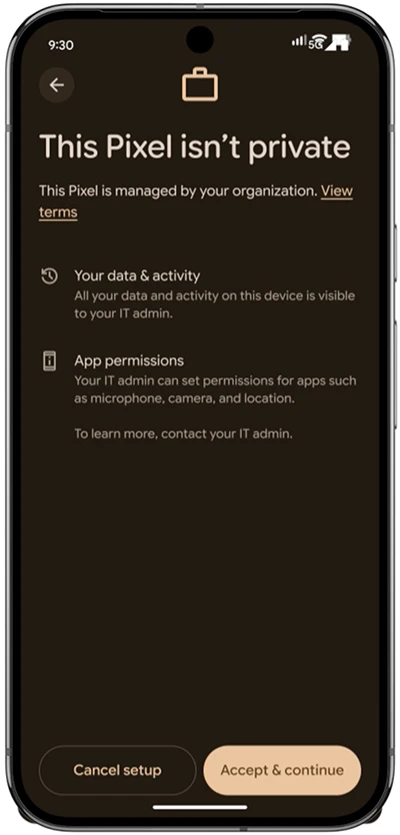
Google is rolling out new Android Enterprise features aimed at improving mobile security, IT management, and employee productivity. According to…
This webinar is designed for leadership and management professionals looking to enhance their organization’s security posture in the cloud. The…
Two Mirai botnets are exploiting a critical remote code execution vulnerability (CVE-2025-24016) in the open-source Wazuh XDR/SIEM platform, Akamai researchers…
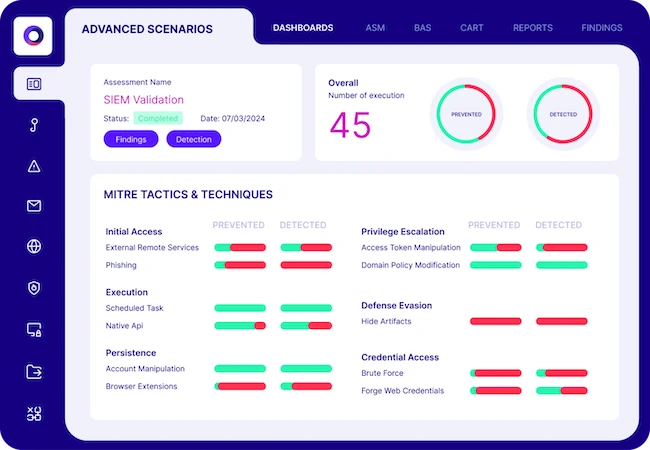
Cymulate releaseed AI-powered detection engineering assistant for security information and event management (SIEM) rule threat coverage validation. Now, the Cymulate…
Automation tester (Infosec) – Vulnerability management WTW | India | On-site – View job details As an Automation tester (Infosec)…
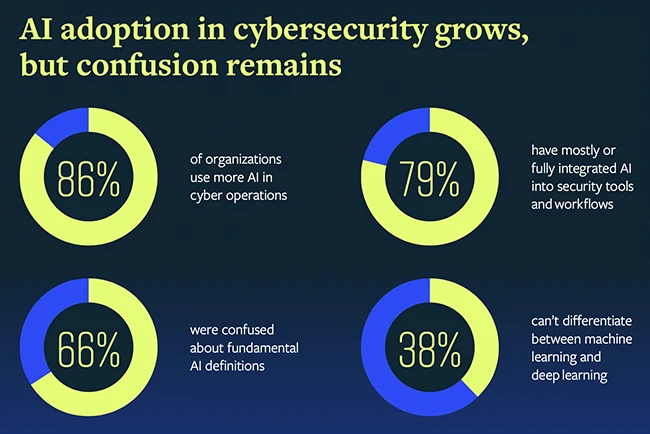
Security teams are leaning hard into AI, and fast. A recent survey of 500 senior cybersecurity pros at big U.S….
At Span Cyber Security Arena, I sat down with Iva Mišković, Partner at the ISO-certified Mišković & Mišković law firm,…
In this Help Net Security video, Eoin Wickens, Director of Threat Intelligence at HiddenLayer, explores the security risks posed by…
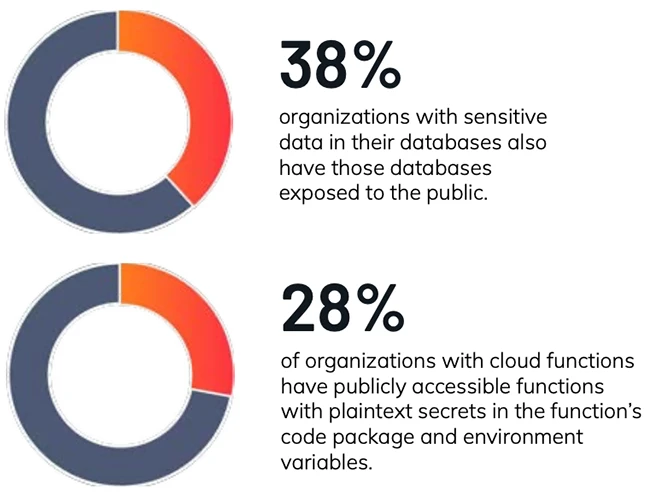
AI adoption is increasing, with 84% of organizations now using AI in the cloud, according to Orca Security. But this…
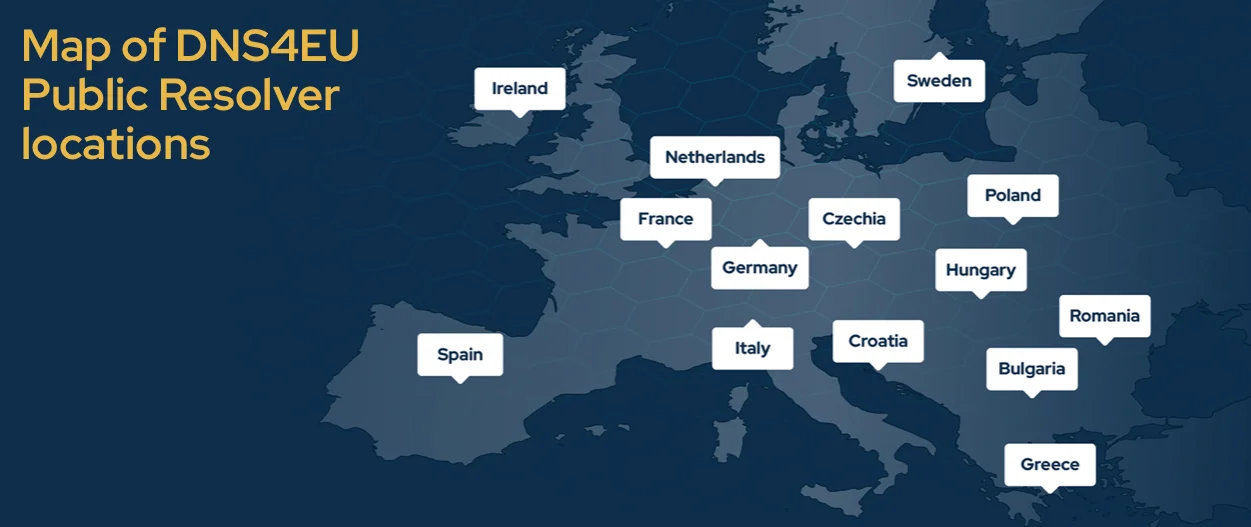
DNS4EU, an EU-based DNS resolution service created to strengthen European Union’s digital sovereignty, has become reality. What is DNS? The…