Category: HelpnetSecurity
A missing authentication vulnerability (CVE-2025-3248) in Langflow, a web application for building AI-driven agents, is being exploited by attackers in…
An easily and remotely exploitable vulnerability (CVE-2024-7399) affecting Samsung MagicINFO, a platform for managing content on Samsung commercial displays, is…
In this Help Net Security interview, Dylan Owen, CISO at Nightwing, talks about what it really takes to build an…
Most attacks don’t start with malware; they begin with a message that seems completely normal, whether it comes through email,…
Application Security Specialist Signify | Netherlands | On-site – View job details As an Application Security Specialist, you will define…
UK-based retailers Marks & Spencer, Co-op, and Harrods have been targeted by cyber attackers in the last few weeks. Whether…
Effective Vulnerability Management offers a view of a key part of cybersecurity, showing how practices, tools, and processes can help…
CISOs know cyber risk is business risk. Boards don’t always see it that way. For years, CISOs have struggled to…
In this Help Net Security interview, Stuart Clarke, CEO at Blackdot Solutions, discusses the strategic use of open-source intelligence (OSINT)…
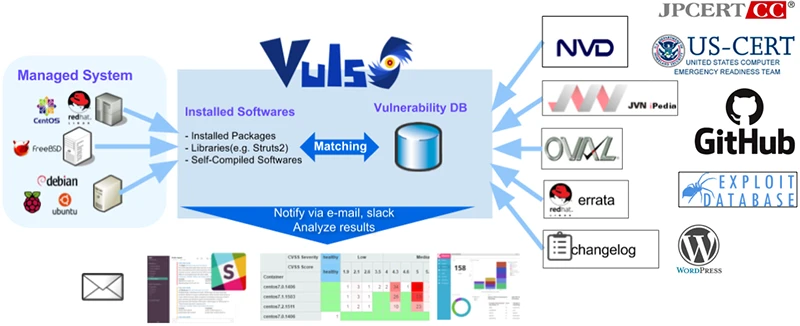
Vuls is an open-source tool that helps users find and manage security vulnerabilities. It was created to solve the daily…
90% of IT and security leaders said their organization experienced a cyberattack within the last year, according to a report…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: RSAC 2025 ConferenceRSAC 2025 Conference…