Category: HelpnetSecurity
Version 8.1 of the CIS Critical Security Controls (CIS Controls) is an iterative update to version 8.0. It offers prescriptive,…
CrowdStrike has published a technical root cause analysis of what went wrong when a content update pushed to its Falcon…
Elastic is accelerating the adoption of AI-driven security analytics by automating SIEM data onboarding with Automatic Import. This new feature…
Two cross-site scripting vulnerabilities (CVE-2024-42009, CVE-2024-42008) affecting Roundcube could be exploited by attackers to steal users’ emails and contacts, email…
Veza has released Access AI, a generative AI-powered solution to maintain the principle of least privilege at enterprise scale. With…
Cequence introduced advancements to its Unified API Protection (UAP) platform, specifically tailored to support the secure use of AI applications…
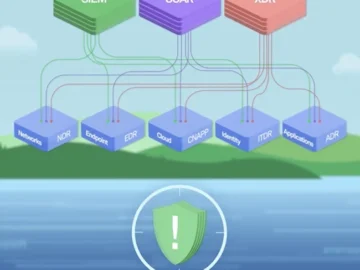
Contrast Security introduced Application Detection and Response (ADR), which empowers security teams to identify vulnerabilities, detect threats, and stop attacks…
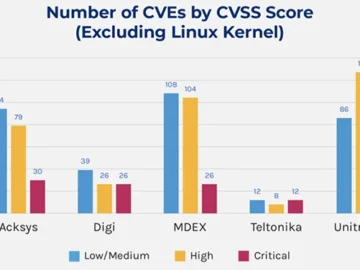
Forescout has published a new report examining the current state of the software supply chain in OT/IoT routers. The study…
Sporting events generate a lot of consumer activity, from hotels and restaurants to retail. Large sporting events are held together…
RustScan is an open-source port scanner designed for speed and versatility. It combines a sleek interface with the power to…
In this Help Net Security interview, Doug Madory, Director of Internet Analysis at Kentik, discusses the FCC’s proposal requiring major…
Outages, human errors, cyberattacks, data breaches, ransomware, security vulnerabilities, and, as a result, data loss are the reality that DevSecOps…