Category: HelpnetSecurity
As privacy laws evolve globally, organizations face increasing complexity in adapting their data protection strategies to stay compliant. In this…
Associate / Pentester (Red Team) – Cybersecurity Audit Siemens | Germany | Hybrid – View job details As an Associate…
Traditional approaches to vulnerability management result in a narrow focus of the enterprise attack surface area that overlooks a considerable…
For May 2024 Patch Tuesday, Microsoft has released fixes for 59 CVE-numbered vulnerabilities, including two zero-days (CVE-2024-30051, CVE-2024-30040) actively exploited…
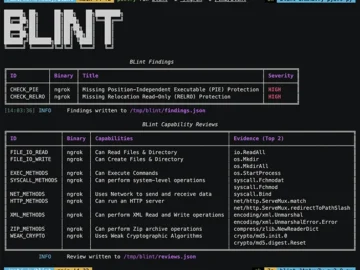
BLint is a Binary Linter designed to evaluate your executables’ security properties and capabilities, utilizing LIEF for its operations. From…
Ask any IT security professional which certification they would consider to be the “gold standard” in terms of prestige, credibility,…
In this Help Net Security interview, Chris Peake, CISO & SVP at Smartsheet, explains how responsible AI should be defined…
Organizations continue to run insecure protocols across their wide access networks (WAN), making it easier for cybercriminals to move across…
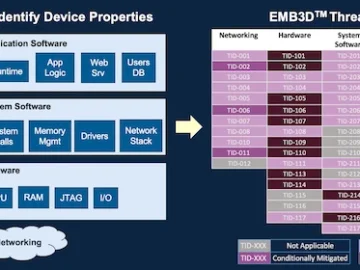
MITRE released EMB3D, a cybersecurity threat model for embedded devices. The model provides a cultivated knowledge base of cyber threats…
In this Help Net Security interview, Dana Wang, Chief Architect at OpenSSF, discusses the most significant barriers to improving open-source…
Developing responsible AI isn’t a straightforward proposition. On one side, organizations are striving to stay at the forefront of technological…
The increased use of AI further complicates CISO role as industries begin to realize the full potential of GenAI and…