Category: HelpnetSecurity
As cloud infrastructures become increasingly API-driven and dynamically spread across expansive attack surfaces, achieving clarity proves difficult. Compounding this challenge…
Open-Source Intelligence (OSINT) refers to gathering, assessing, and interpreting public information to address specific intelligence queries. All the tools listed…
RARLAB has fixed a high-severity RCE vulnerability (CVE-2023-40477) in the popular file archiver tool WinRAR. About CVE-2023-40477 A widely used…
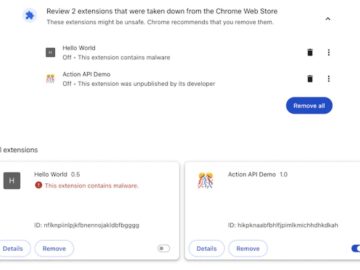
Google will be extending the Safety check feature within the Chrome browser to alert users when a previously installed extension…
There is a standard playbook and best practice for when an organization discovers or is notified about a software vulnerability:…
In this Help Net Security interview, David Gugelmann, CEO at Exeon, sheds light on the current cyber threats and their…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Deception technology and breach anticipation…
Burnout is endemic in the cybersecurity industry, damaging the mental and physical health of cyber professionals and leaving organizations underskilled,…
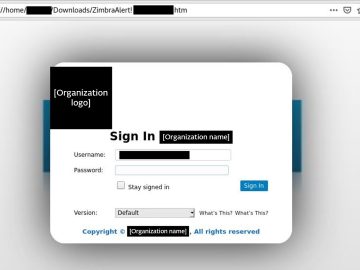
ESET researchers have uncovered a mass-spreading phishing campaign aimed at collecting Zimbra account users’ credentials. Zimbra Collaboration is an open-core…
From understanding the challenges of disparate OT protocols and the increasing convergence with IT to grappling with the monumental role…
Here’s a look at the most interesting products from the past week, featuring releases from Action1, MongoDB, Bitdefender, SentinelOne and…
Phishing remains the most dominant and fastest growing internet crime, largely due to the ubiquity of email and the ceaseless…